OpenCTI for National Security Agencies: 5 Use Cases
Security agencies face a uniquely challenging cybersecurity landscape. From defending critical infrastructure against state-sponsored espionage to quickly responding to cybercrime campaigns, the stakes are high and the threats complex.
While the volume of cyber threat data can be overwhelming, turning it into meaningful, actionable intelligence is essential. That’s where they are turning to Filigran, with OpenCTI Enterprise Edition (EE) fast becoming platform of choice for threat management.
Here we provide you five different ways for the security agencies to leverage OpenCTI EE to protect national interests and improve their cyber defenses:
Automating Threat Sharing for National CERTs
When national-level threats emerge, CERTs must act swiftly and share threat intelligence across sectors to mitigate risks in real time. OpenCTI EE automates this process, ensuring fast and coordinated responses.
CERT teams use platforms like OpenCTI to automatically share cyber threat indicators (e.g., malicious IPs, phishing domains) with other national and international cybersecurity teams.
For example, when a phishing campaign targets government employees, the national CERT can immediately shares details with banks, telecom providers, and other essential services to block the threat.
Leveraging Intelligence for Cybercrime Investigations
Cybercrime investigations demand not only accurate intelligence but also rapid access to contextual data about threat actors, their tactics, and infrastructure. OpenCTI EE empowers law enforcement agencies to act swiftly by centralizing threat intelligence and enabling real-time collaboration across jurisdictions and sectors.
By integrating with third-party tools and enabling secure, role-based access, OpenCTI EE ensures that intelligence is disseminated efficiently and only to those who need it—accelerating investigations and improving outcomes.
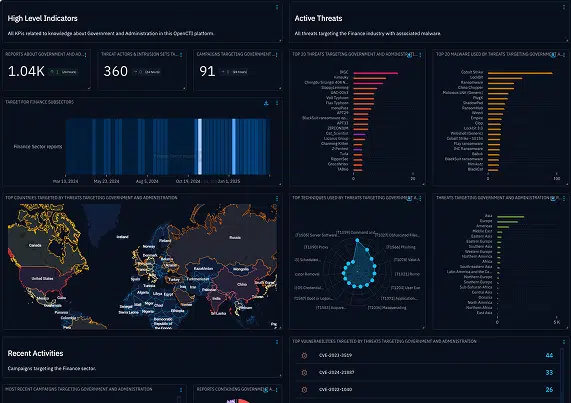
Managing Classified Information Securely
Defense organizations must analyze threats without compromising national secrets. OpenCTI EE enables intelligence workflows on air-gapped systems, supporting multiple classification levels.
Defense agencies handle sensitive intelligence that must be carefully managed. They use air-gapped networks, completely isolated from the internet to analyze possible threats, protect classified data while creating and sharing intelligence at different security levels. This approach enables cyber units to prevent leaks and OpenCTI EE fully supports this.
Sharing Intelligence with Strategic Partners
While national CERTs and law enforcement agencies focus on broad threat mitigation and criminal investigations, intelligence agencies often need to share highly sensitive threat data with a select group of trusted partners. OpenCTI EE enables this with fine-grained access controls and multi-organization support, ensuring that only the right people see the right data.
These partners may include:
- Critical infrastructure operators (e.g., energy, transportation, healthcare)
- Private-sector cybersecurity teams in finance, telecom, and defense industries
- International allies and intelligence-sharing alliances
- Sector-specific ISACs (Information Sharing and Analysis Centers)
- Technology vendors providing detection, response, or enrichment services
This selective sharing model ensures that intelligence is actionable and relevant to each partner, while maintaining operational security and compliance with national policies.
Strengthening Cyber Defense through collaboration
In today’s interconnected digital environment, cyber threats rarely target organizations in isolation. Government agencies, critical infrastructure operators, and private-sector partners are all part of a shared ecosystem vulnerable to coordinated attacks. To effectively defend national interests, real-time and secure intelligence sharing across agencies and industries is crucial.
With features like native data segregation and flexible access control, OpenCTI EE ensures that sensitive information is shared only with authorized parties while still maximizing the collective visibility needed to anticipate and neutralize threats. By breaking down silos, agencies can leverage the combined knowledge of the broader cybersecurity community, improving situational awareness and reinforcing national resilience.
Additional resources
- OpenCTI EE Webinars: learn how OpenCTI EE boosts threat detection and intelligence workflows — including Automated Playbooks and RBAC.
- Government Use Cases Webinars: real-world insights from national agencies on key cybersecurity challenges.
- More Use Cases: visit our Use Cases Library
- Questions? Contact us
Read more
Explore related topics and insights
