Defining Observables, Indicators, and Infrastructure in Cyber Threat Intelligence
In a previous article, we explored the differences between Threat Actors and Intrusion Sets, clarifying their distinct roles in structured threat intelligence frameworks like STIX and OpenCTI. Building on that foundation, this article focuses on another critical distinction in cybersecurity: Observables, Indicators, and Infrastructure. While these terms are often used interchangeably, they represent different components of threat intelligence, each serving a unique purpose in detecting, analyzing, and mitigating cyber threats.
This article aims to clarify these differences, explain how they interconnect, and provide guidance on their appropriate use in threat intelligence models.
Defining the Terms
Observables
Observables are raw data points or measurable events within a system or network. As seen below, observables on their own don’t necessarily indicate malicious behavior and can include items like legitimate IPs or domains associated with an organization. However, observables more serve as pieces of information that can help analysts understand the activity occurring in their networks and serve as a foundation for further analysis.
Examples include:
- IP Addresses: Numerical identifiers, which can be static or dynamic, assigned to devices on a network.
- Ex: 192.168.1.1 is a common local IP address that can be an observable found in network logs.
- Domain Names: Human-readable addresses that map to IP addresses and are used to access online services.
- Ex: example.com is a domain that can be seen in DNS queries.
- File Hashes: Unique identifiers generated by algorithms (e.g., MD5, SHA-256, SHA-1) representing specific files.
- Ex: 61e2f9029baf7ce21d8de2eddea55405f20ed5db26ecbdaea42404ca28a08d7c is a SHA-256 hash representing AnyDesk.exe, which can be benign or used for malicious purposes.
- Registry Key Values: Configuration settings in Windows systems’ registry that are often modified by malware for persistence and can be monitored for changes
- Ex: **Registry Key:**HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- Registry Value:
- Name: MaliciousApp
- Type: REG_SZ (String)
- Data: C:\Users\Public\malicious.exe
- Network Traffic: Patterns observed in network communications, such as activity related to command-and-control (C2) communications, exploitations, and/or data exfiltration
- Ex: GET /malicious/path HTTP/1.1 is an example of a suspicious HTTP request pattern.
Indicators
Indicators, or Indicators of Compromise (IOCs), are Observables enriched with context to signify potential threats. An Indicator typically includes a pattern or logic that defines the conditions in which an Observable might be a threat.
In the scope of OpenCTI, an Indicator comes in the form of a detection object defined by a search pattern, which can be expressed in various formats such as STIX, Sigma, YARA, and more. In addition to the pattern, Indicators will often include supplementary information that enhances its context for detection, such as validity dates, the relevant kill chain phase, and actionable attributes (e.g., “revoked” status, etc.). The goal behind Indicators is to link Observables like those above to malicious activities and provide actionable intelligence to help security teams more efficiently detect and respond to cyber threats.
Examples include:
- A STIX 2.1 pattern containing an IP address known to be used for command-and-control.

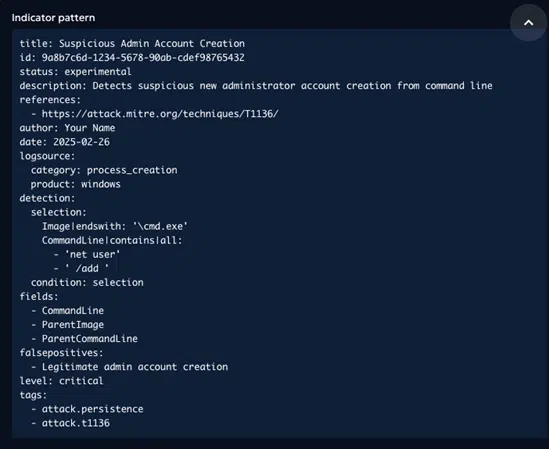
- A Sigma rule detecting the creation of new administrator accounts from the command line interface, indicating attempts to create unauthorized admin accounts.
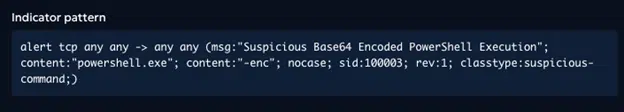
- A Suricata rule detecting the execution of Base64-encoded PowerShell commands, which are often used by threat actors for obfuscation.
Infrastructure
Generally, Infrastructure refers to the resources, tools, and services utilized by threat actors to carry out their malicious activities. Like Observables, Infrastructure in itself is not inherently malicious and can encompass a wide range of resources such as those within a target environment. However, when referenced in the context of cyber attacks, Infrastructure typically implies the assets used by adversaries to conduct their operations.
Understanding an attacker’s Infrastructure is essential for attribution and proactive threat hunting, as it reveals the underlying framework, methods, and tools used by a threat actor to facilitate their malicious operations.
Examples include:
- Command-and-Control (C2) Servers: Domains and IPs associated with servers used by attackers to maintain communication with compromised systems, issue commands, and exfiltrate data.
- Ex: 74.178.90.36:443 is an IP address and port hosting a C2 panel for remote administration.
- Phishing infrastructure: Websites, emails, and assets used to deceive victims into revealing sensitive information such as credentials or financial data.
- Ex: login-microsoft-security[.]com is a fake Microsoft login page for credential harvesting.
- Malware distribution infrastructure: Websites or servers hosting malicious payloads for drive-by downloads or malware delivery.
- Ex: malicious-download[.]xyz/malware.exe is an example of a payload delivery server.
- Anonymization Services: Services like Virtual Private Networks (VPNs) or The Onion Router (TOR) that attackers use to conceal their identities and locations.
- Ex: TOR exit node IP: 176.10.104.240 used for brute-force login attempts.
Key Differences
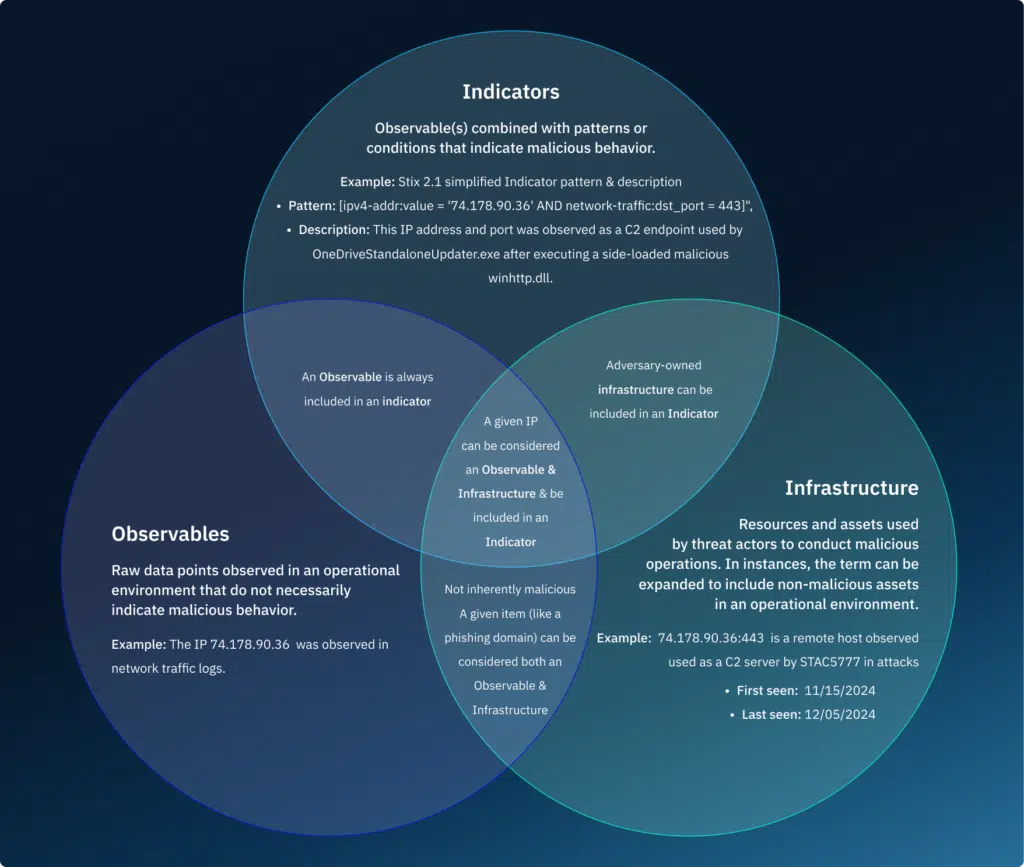
Real-Life Examples
Observables in Action
An organization detects a series of failed login attempts from a single IP address over a short period. The IP address alone is an Observable—it may be benign or part of an attack. The security team enriches this data by checking reputation sources, revealing that the IP is associated with previous brute-force attempts. This information helps analysts determine whether to block the IP or investigate further.
Indicators in Action
An organization observes the modification of their Windows registry by a cybercriminal actor to add a registry entry named “HKLM\Software\TitanPlus”, which contains list of IP addresses that a malicious file uses for C2 connections. The security team creates an Indicator in STIX format that flags modifications of the Windows registry using reg.exe to create a registry key named “HKLM\Software\TitanPlus” containing list of C2 IP addresses in order to help detect and similar behavior in future incidents.
Infrastructure in Action
An organization detects communications with an IP address tied to a known ransomware group. By mapping the adversary’s infrastructure via open-source tooling, the security team identifies additional domains and IPs associated with the attacker, which allows them to block related malicious traffic before the attack escalates.
Practical Applications
Detection and Monitoring
Security teams collect and analyze observables to identify potential threats. For example, monitoring network traffic for unusual IP addresses or unexpected HTTP requests can reveal suspicious activities. Indicators enhance this process by providing known malicious signatures, enabling automated systems to flag threats promptly.
Threat Hunting
Analyzing infrastructure components allows cybersecurity experts to anticipate and counteract potential attacks. For instance, identifying a new phishing site targeting an organization enables preemptive measures, such as blocking the domain and warning users. Understanding attacker infrastructure facilitates proactive defense strategies.
Incident Response
Indicators guide incident response efforts by helping analysts determine the extent of an attack and implement mitigation strategies. For example, recognizing a malware file hash in the system prompts immediate isolation and removal procedures. Infrastructure analysis assists in disrupting attacker operations by identifying and taking down C2 servers or dismantling botnets.
Challenges and Considerations
Volume and Variety
Organizations handle vast amounts of Observables daily, and managing Observables at scale can be difficult without automation. Differentiating between benign and malicious data requires efficient correlation and analysis techniques, and platforms like OpenCTI with its ingestion and enrichment connectors can aid in sifting through large datasets and correlating Observables with relevant intelligence.
Context Matters
Threat actors employ sophisticated techniques to obfuscate their Infrastructure, making attribution challenging. For example, using anonymization services or hijacking legitimate servers can mask the true source of an attack. Accurate attribution necessitates comprehensive analysis and often collaboration with other organizations and law enforcement agencies.
Dynamic Threat Landscape and the Ephemeral Nature of Observables
Attackers continuously adapt their tactics and infrastructure, necessitating ongoing monitoring and intelligence-sharing. To illustrate, threat actors frequently rotate and discard their Infrastructure to prevent tracking and detection, which can make it challenging for defenders to maintain accurate data over time.
Therefore, it’s important to keep in mind the ephemeral nature of Observables, such as IPs and domains, and consider an indicator’s lifecycle in line with when it was last seen and its likelihood for reuse over time. For effective long-term analysis and detection, defenders should prioritize higher fidelity Indicators based on attributes that are higher up on the Pyramid of Pain and are less likely for attackers to easily swap out.
Observables, Indicators, and Infrastructure in OpenCTI
“Example.com” is observed in an organization’s network traffic logs, initially appearing legitimate. The domain is added as an Observable in OpenCTI. Upon further analysis by the security team, the domain was revealed to have connections to a known phishing domain, “Malicious-example.com“, linked to a reported threat actor. Upon creating an Observable for “Malicious-example.com“, the security team also creates an Indicator for the domain and links it to an Infrastructure entity, which will now assist in detecting and blocking further malicious activity.
These relationships are captured in OpenCTI (STIX) using explicit relationships such as related-to, communicates-with, and uses, allowing analysts to map and correlate cyber threats systematically. By leveraging these interconnections, a team can effectively leverage Observables, Indicators, and Infrastructure to build more robust threat intelligence, generate effective detections, and proactively disrupt adversary operations.
Conclusion
Observables, Indicators, and Infrastructure each serve distinct roles in cybersecurity. Observables act as raw data, Indicators provide actionable intelligence, and Infrastructure represents the operational assets of attackers. By comprehending these concepts and leveraging them effectively, you and your team can enhance detection, response, and mitigation efforts, thereby strengthening your organization’s overall security posture.
This article was made possible thanks to the collaboration within our Women in CTI Slack channel. To join and be part of the conversation, click here.
About Morgan Demboski
Morgan is a Threat Intelligence Analyst for the Sophos Managed Detection and Response (MDR) team, where her focuses include tactical cyber intelligence, data enrichment, and monitoring emerging threats. With a Masters in Intelligence and Security Studies, her areas of interest span beyond the cyber realm to include geopolitics and international security. In past roles, Morgan worked in the Network Detection and Response (NDR) space, where she focused on tracking attack patterns, analyzing command-and-control infrastructure, and threat research reporting.
Read more
Explore related topics and insights


