Leveraging OpenCTI: An MSSP’s Journey Through Threat Intelligence Maturation
Organizations are no longer satisfied with generic security alerts, they are seeking further cyber security services from Managed Security Service Providers (MSSPs) that provide their organizations greater protection from ever increasing amounts of sophisticated malware and new techniques being developed by adversaries. Managed MSSP’s are facing increasing pressure to deliver innovative solutions to meet customers’ evolving needs. Filigran offers MSSPs the ability to provide comprehensive threat intelligence capabilities to their clients by providing contextualized, actionable intelligence that addresses the specific threats that customers are facing.
Filigran’s OpenCTI is a powerful platform that enables MSSPs to initiate, develop, mature, and monetize a threat intelligence service offering.
This blog post outlines a five-phase maturation journey that MSSPs can follow to start and then grow their threat intelligence capabilities from optimizing the internal use of threat intelligence, all the way to offering customers advanced threat intelligence services.
Phase 1: Centralization Without Capital Investment
The journey begins with centralizing all available threat intelligence data into a single, accessible repository. This includes:
- Customer-provided intelligence
- Internal investigation findings
- Open-source intelligence (OSINT)
- Premium threat feeds
A key advantage of this centralization is that anytime an analyst or researcher within the company performs an investigation or responds to an incident, the generated data can be immediately added back to OpenCTI. This creates a virtuous cycle where each analysis enriches the collective intelligence repository, continuously augmenting the value of the company’s intelligence assets. Over time, this growing body of proprietary intelligence becomes an increasingly valuable differentiator that enhances the MSSP’s detection and response capabilities.
Case study: This model is currently deployed by some innovative MSSP’s who offer Incident Response (IR) services. Their analysts use OpenCTI extensively during live IRs to record the latest malware and for investigations.
Key Benefits:
- Single source of truth for all threat intelligence
- Enhanced collaboration across security teams
- Elimination of intelligence silos
- No upfront capital expenditure required
Phase 2: Security Stack Integration
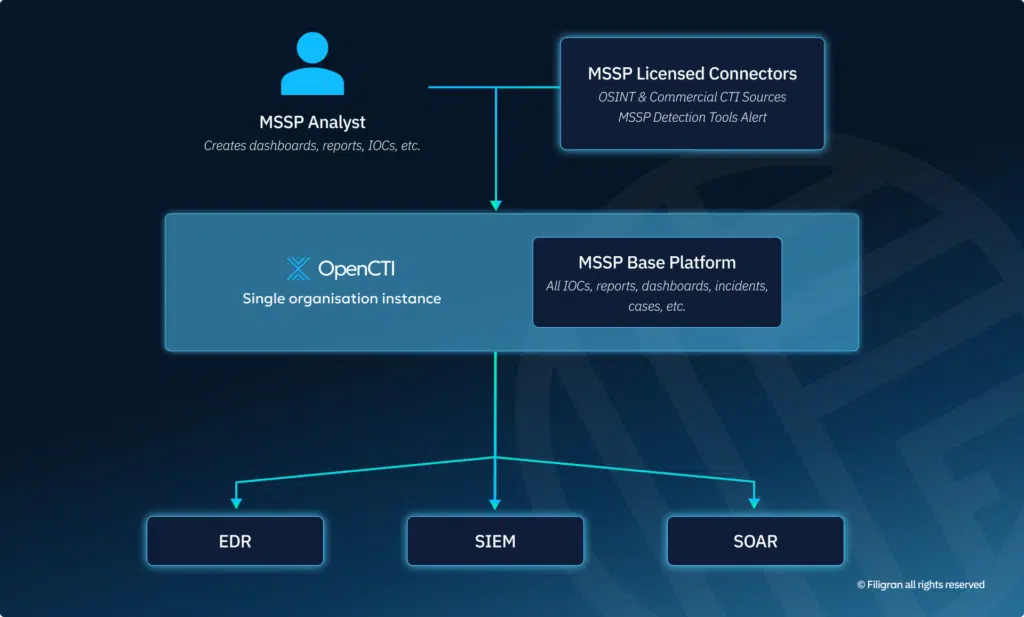
Once the centralized threat intelligence repository is established, the next phase involves pushing this intelligence to the customers’ security stack. This creates an additional layer of protection beyond native detection capabilities by using the gathered threat intelligence.
OpenCTI comes with a rich ecosystem of integrations into leading EDR, SIEM, and SOAR platforms. These automation features enable seamless integration with existing security tools, ensuring that threat intelligence is operationalized effectively across the customers environment. This delivers immediate value to customers and serves as a competitive differentiator for MSSPs.
OpenCTI includes robust automation capabilities for streamlining intelligence curation, enrichment, and dissemination. This automation reduces the manual workload on analysts, allowing them to focus on high-value analysis rather than routine data processing. The platform’s ability to automatically correlate new information with existing intelligence ensures that threat data is continuously enriched and contextualized, maximizing its operational value when integrated with security tools.
Key Benefits:
- Enhanced detection capabilities
- Reduced false positives
- Improved response times
- Competitive advantage in the marketplace
Phase 3: Customer Intelligence Delivery
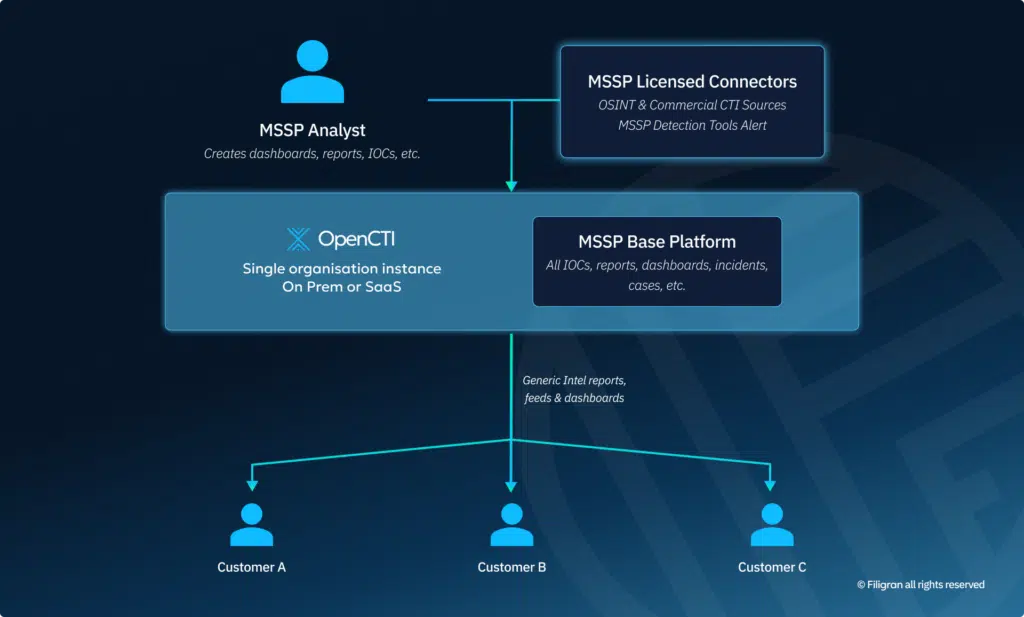
With a mature internal threat intelligence capability, MSSPs can begin delivering intelligence services to customers through multiple channels:
- Curated Feeds: Provide machine-readable threat intelligence that customers can integrate into their security tools
- Dynamic Dashboards: Offer online access to threat intelligence through intuitive, interactive dashboards
- Intelligence Reports: Deliver detailed analysis and contextualized intelligence in report format
At this stage, the same intelligence is made available to all customers through a single, consistent channel—the OpenCTI platform.
OpenCTI offers a wealth of capabilities for curating and refining intelligence before delivery to customers. Its also worth exploring the transition from the Community Edition to Enterprise Edition in this phase. The Enterprise Edition includes AI-powered features that can automatically generate customer reports, executive summaries, and threat bulletins, saving significant analyst time. This automation enables MSSPs to scale their intelligence delivery without proportionally increasing staff, improving margins while maintaining high-quality deliverables.
Business Opportunities:
- Include threat intelligence as a value-added service
- Create a new revenue stream by charging for premium intelligence
- Bundle with advisory services to help customers operationalize the intelligence
Phase 4: Customized Intelligence Services
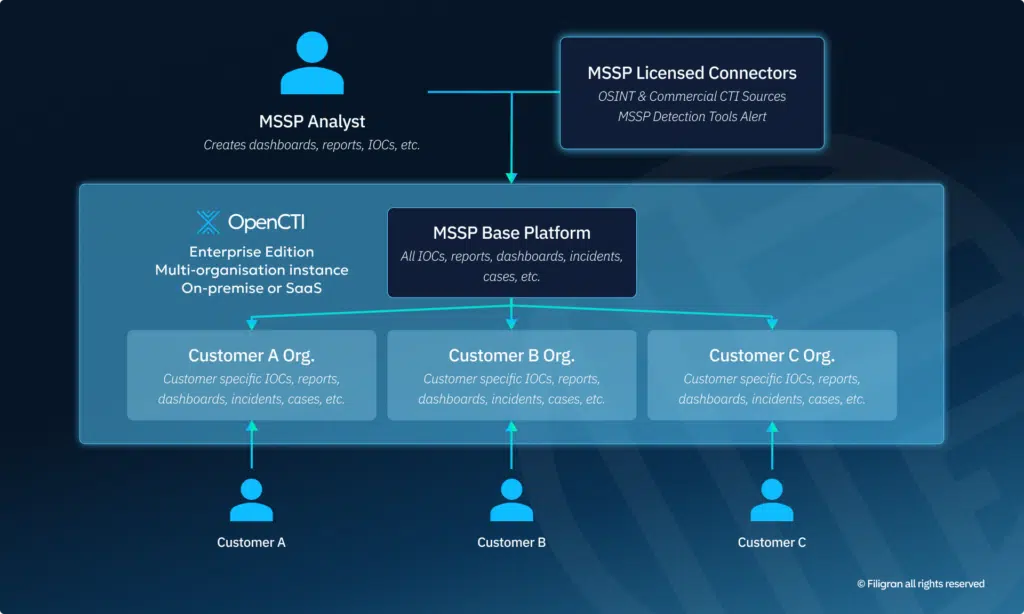
As MSSPs develop more sophisticated internal CTI competence, OpenCTI makes it remarkably easy to customize intelligence for each client’s unique needs. Through the platform’s advanced filtering and customization capabilities, MSSPs can tailor intelligence to address the specific industry verticals, geographic locations, technology stacks, and business priorities of individual clients. This level of customization creates a highly differentiated, premium offering that dramatically increases the perceived value of the service. By delivering precisely targeted intelligence rather than generic feeds, MSSPs can command higher prices while providing more relevant and actionable information that clients are willing to pay a premium to receive.
The OpenCTI Enterprise Edition supports this through Organizational Role-Based Access Control (RBAC), allowing MSSPs to create customized views for each client. For example:
- Dashboards focused on threats targeting US financial institutions
- Intelligence feeds tailored to healthcare organizations in Europe
- Specialized reports for critical infrastructure sectors across Asia
This customization represents significant added value, as it helps customers focus on the threats most relevant to their business. The OpenCTI platform also enables customers to submit Requests for Information (RFIs) and Requests for Takedown (RFTs), providing a single interface for all threat intelligence interactions.
Key Benefits:
- Increased customer satisfaction through relevance
- Time savings for customer security teams
- Enhanced perception of the MSSP as a strategic partner
- Single platform for intelligence delivery and customer requests
The only limitation at this stage is that the model is primarily read-only—the MSSP customizes how intelligence is presented, but customers cannot contribute their own intelligence back to the platform.
Phase 5: TIP as a Service
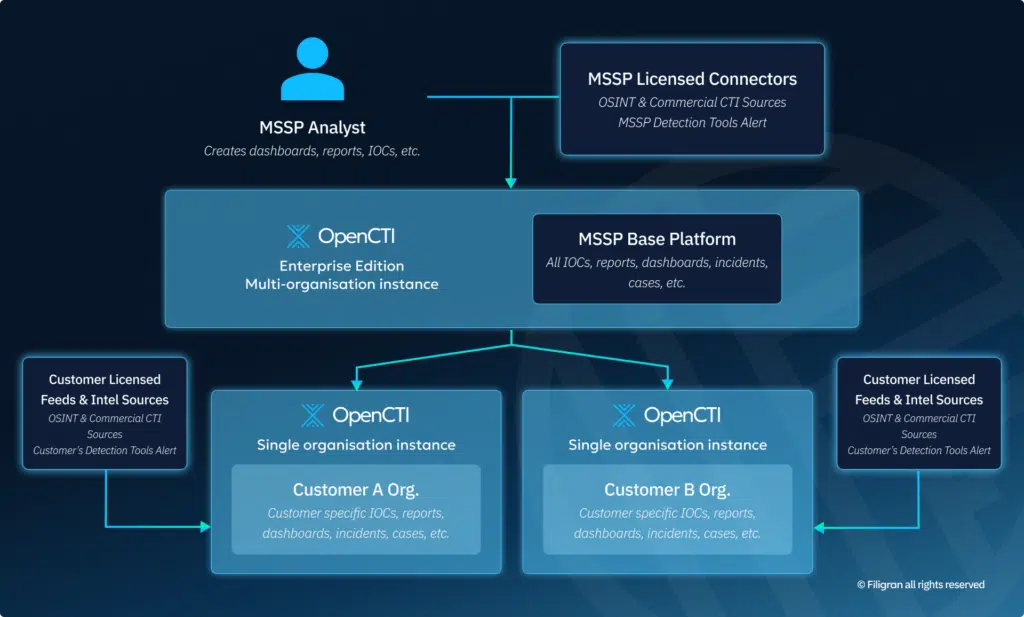
The final phase represents the most advanced offering: Threat Intelligence Platform (TIP) as a Service. This model is ideal for mature customers who understand the strategic value of threat intelligence in security planning and investment decisions.
OpenCTI’s support for operational and strategic intelligence (beyond tactical and technical use cases) creates an opportunity for MSSPs to offer a comprehensive managed service.
In this model, the MSSP:
- Sets up a dedicated OpenCTI instance for each client
- Synchronizes relevant intelligence from their production instance
- Integrates client-specific intelligence sources (premium feeds, internal sources, industry-specific intelligence)
- Provides ongoing management or co-management of the platform
This approach offers maximum flexibility and enables MSSPs to deliver high-value services such as:
- Intelligence requirements analysis
- Collection planning
- Program implementation and maturation guidance
- Strategic intelligence advisory
Business Impact:
- Higher-margin services revenue
- Deeper client relationships
- Competitive differentiation
- Long-term customer retention
Conclusion
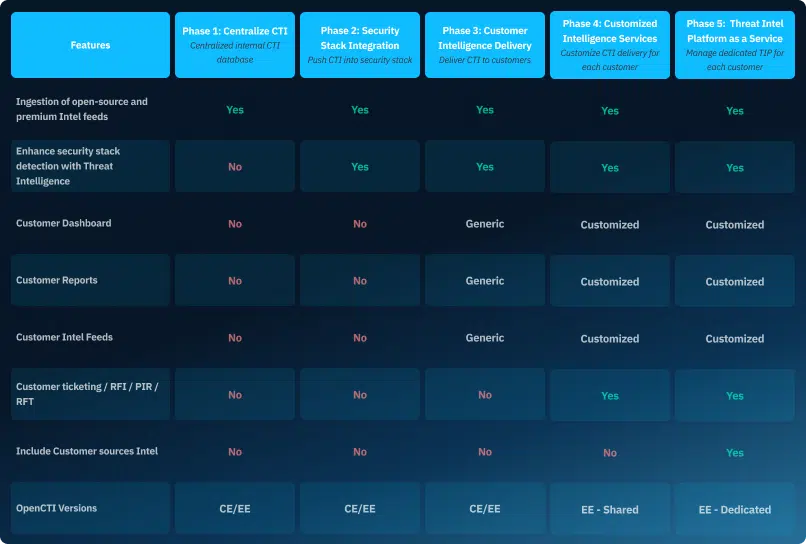
The journey from basic threat intelligence aggregation to TIP as a Service represents a clear path for MSSPs to mature their threat intelligence practice and business using Filigran OpenCTI. Each phase builds upon the previous one, allowing for incremental growth in capabilities, customer value, and revenue opportunities:
- Phase 1: Centralize all threat intelligence in a single repository, creating a collaborative environment where every analysis enriches your intelligence assets
- Phase 2: Integrate intelligence with your security stack through automation, enhancing detection with minimum manual effort
- Phase 3: Deliver intelligence to customers as a service, leveraging AI to generate reports and scale efficiently
- Phase 4: Customize intelligence for each client’s unique context, creating premium offerings that command higher prices
- Phase 5: Provide fully managed TIP as a Service with dedicated instances that integrate client-specific sources
By following this maturation journey, MSSPs can transform threat intelligence from a cost center into a strategic differentiator and revenue generator, all while helping their customers better defend against evolving cyber threats. Importantly, Filigran OpenCTI is specifically designed to accompany MSSPs every step through this maturation journey, from community edition to enterprise capabilities, growing alongside your threat intelligence practice.
Webinar: Turn Your Security Operations into a Revenue Engine
Join cybersecurity veteran Jason Maurath and Jan Johansen to discover how MSSPs can grow their threat intelligence capabilities and transform them into revenue-generating services with OpenCTI. This fireside chat reveals a 5-phase maturity model that helps MSSPs evolve from basic threat data collection to delivering premium security services that command higher margins and create lasting customer loyalty.
Read more
Explore related topics and insights
