From Intelligence to Impact: How Metrics Prove the Value of Threat Intelligence
Threat intelligence is no longer a luxury – it’s a necessity. But even when organizations invest heavily in intel platforms, feeds, and analysts, one big question remains:
How do we prove its value?
That’s where metrics come in. Not vanity stats or big numbers for the sake of dashboards – but meaningful, outcome-driven metrics that help organizations understand the impact of threat intel on their security posture, operations, and business decisions.
One of the key factors in making CTI successful? Having the right metrics for the right stakeholders – and knowing how to use them.
Why Metrics Matter in Threat Intelligence
Without metrics, threat intelligence can feel like a black box: too technical for some, too complex to be useful for others, sometimes vague, or entirely disconnected from business goals. But with the right metrics demonstrated in clear way, threat intel becomes a strategic asset.
Metrics help:
- Make intelligence value visible: What intelligence is being produced, how timely it is, and how it’s used?
- Link threat intel to impact: Is it reducing risk? Improving response? Supporting decision making?
- Drive continuous improvement: Are our sources useful? Are our processes efficient and scalable?
Real-World Metrics That Show the Value of Threat Intel
Let’s break this down with case studies showing examples of concrete metrics that matter to CISOs, SOC leads, and business stakeholders alike.
1. Getting the CTI Job Done: Operational Efficiency Metrics
These metrics show how efficiently threat intel tasks get done, from speeding up workflows to cutting down on noise.
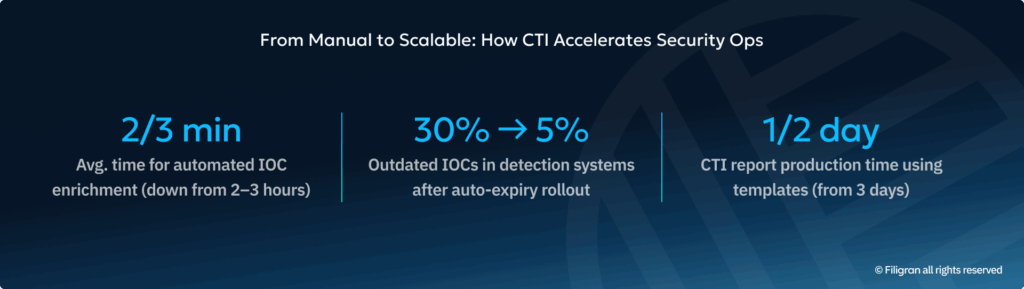
📌 Example: Time to Enrichment (TTE)
Enriching indicators manually averages 1-2 hours per IOC. Automating enrichment via your platform results in time dropping to 1-3 minutes.
➡️ Result: Lower analyst workload and quicker incident handling → X hours saved per month.
📌 Example: False Positive Ratio in Indicators
Customer ingested 500,000 IOCs from a high-cost feed. SIEM analysis showed that less than 1% triggered actionable alerts – and those often lacked context or relevance.
➡️ Result: Customer reallocated budget towards better curated and context-rich sources, reducing noise and saving cost.
📌 Example: IOC lifecycle hygiene
Audits revealed that almost 30% of outdated IOCs were still active in detection systems. Automated expiration workflows brought this down to under 5%.
➡️ Result: Cleaner and more accurate threat data and fewer irrelevant alerts.
📌 Example: CTI deliverable production time
Finalized CTI reports took up to 3 days to draft, review and publish due to fragmented inputs and manual formatting. Ready-to-use standardized templates and workflows cut that down to half a day.
➡️ Result: Faster delivery of actionable intel with reduced time spent on coordination and (analytically uninteresting) formatting.
2. Making CTI Count in the Field: Tactical Impact Metrics
These metrics show how threat intel helps detect, block, or respond to threats.

📌 Example: Proactive Threat Mitigation
A manufacturing company was receiving weekly CTI updates. One highlighted details of a ransomware group targeting industrial control systems – a threat that hadn’t yet hit their region. Their team hardened vulnerable endpoints before the campaign reached them.
➡️ Result: Early CTI warning enabled real-world risk reduction.
📌 Example: Incident Prevention
In another case, CTI team flagged a command-and-control domain tied to an active phishing campaign. Security teams blocked the domain at the perimeter and stopped a targeted phishing attempts against senior leadership.
➡️ Result: Timely intelligence prevented a high-impact incident.
📌 Example: Detection Coverage
Over the last quarter, the detection engineering team of an insurance firm implemented 67 new detection rules in SIEM and EDR platforms based on CTI-provided IOCs, TTPs, and campaigns insights.
➡️ Result: Clear and quantifiable link between CTI and improved detection, demonstrating how intel directly powers threat hunting and alerting pipelines.
3. Making CTI Matter Beyond Security: Strategic & Business Alignment Metrics
These metrics highlight how CTI informs decisions beyond security operations: from boardrooms to legal teams to business risk planning.

📌 Example: Executive-Level Understanding
A biotech company security team started including 1-page intelligence briefs in board updates. By shortening the brief to one page and by shifting from technical jargon to clear “what it means for us” messaging, leadership engagement increased 3x.
➡️ Result: Executive teams started requesting CTI input in strategic areas like mergers, acquisitions, and vendor assessments.
📌 Example: Intelligence-Informed Business Planning
A logistics firm preparing expansion into a new region received intelligence on a state-sponsored APT activity targeting local market. This intel shaped the company’s risk assessments and led to increased security enhancements in advance.
➡️ Result: Business risk addressed proactively and mitigated before operations began.
📌 Example: Legal and Compliance Support
A media company’s CTI team began holding monthly briefings with internal legal and compliance teams, highlighting threat actor activity linked to cybercrime cases. Their reporting supported coordination with law enforcement, contributing to successful legal action against several threat actors.
➡️ Result: CTI became a strategic asset, reducing organizational risk while actively supporting legal and law enforcement efforts to disrupt threat actors in and beyond the company’s perimeter.
How to Present Threat Intel Metrics Effectively
Metrics are communication tools
Don’t treat them as raw outputs: treat them as messages. Each metric should help your stakeholder understand something they care about: a risk avoided, a trend emerging, or a capability gap addressed. This means that you have to tailor the metric to your audience.
Lead with insights, not numbers
The goal isn’t to show data: it’s to highlight meaning. What changed? Why does it matter? What should be done next? Put the takeaway first, not buried in a footnote.
Frame metrics within decisions
Good CTI metrics don’t just report what happened: they support actions – adjust priorities, shift resources, close gaps, escalate issues… A metric is valuable only when it informs a decision. A single metric means little in isolation, but when it’s tied to prevention, savings, or decision support, it becomes powerful.
Visuals are part of the message
Graphs, timelines, and heatmaps should reinforce your point, not just decorate the slide. Choose formats that reveal patterns or comparisons, not ones that overwhelm the audience.
Consistency builds trust
Use the same definitions, intervals, and formats over time. Inconsistent metrics confuse stakeholders and dilute your credibility, even if the data is technically accurate.
Size matters!
Make it short – in fact, as short as possible. Always assume that your audience has super short attention span.
What to Avoid: Common Pitfalls in CTI metrics
Too much volume, not enough value
Reporting that “We ingested 5 million IOCs” sounds impressive, but if none of them were relevant, timely, or used in detection or incident response, this number is meaningless. Volume without focus and precision just creates noise, wastes analysts’ time and drives up platforms cost.
Unactionable & Untailored metrics
A metric, like any other intelligence product, must serve a purpose. If it doesn’t influence decision or drive action, it’s simply operationally useless. Similarly, metrics that aren’t aligned to stakeholders’ needs won’t be read, trusted, or acted upon. Untimely and irrelevant metrics are just noise in a polished format.
Metrics without owners
If no one is responsible for interpreting or acting on a metric, it becomes a dead number. Metrics need clear ownership to ensure accountability, follow-up and refinement. Otherwise, even well-designed measures fail to produce outcomes.
Vanity metrics
Dashboards crammed with counts (reports published, IOCs ingested, alerts generated…) may look great, but they rarely inform actual decisions. These are vanity metrics – high activity, low insight. Combined with dense, technical visualizations, they overwhelm non-technical stakeholders.
No Baseline or Benchmark
A metric without a baseline is just a number. Saying “MTTD is 8 hours” means little, unless you know what it used to be, what the goal is, or how peers compare. Without that context, you can’t evaluate progress or justify change.
Final Takeaway: Metrics Make Intelligence Matter
Threat intelligence is only as valuable as its outcomes – and metrics are how we prove and improve that value. Whether you’re showing ROI, securing budget, or informing decisions, having the right metrics can make all the difference.
To make your CTI truly impactful:
- Focus on outcomes, not outputs. Show how threat intel reduces risk, saves time, or supports action – not just how much data was processed.
- Tailor metrics to the audience. Executives want strategic clarity. SOC leads need operational insight. Business leaders look for risk context. Speak their language.
- Provide context and ownership. A useful metric has a purpose, a benchmark, and a responsible owner. Without those, it’s just noise.
- Keep it clear, short, relevant, and actionable. The best metrics lead to change: in priorities, in defenses, in results.
Remember, when you track what matters, you’re not just doing threat intel – you’re actually making it work for the business.
This article was made possible thanks to the collaboration within our Women in CTI Slack channel. To join and be part of the conversation, click here.
About Eliska Puckova
Eliska is a Cyber Threat Intelligence specialist with years of experience in the field, specializing in adversary profiling, cyberHUMINT, and support to incident response teams. Her background includes training in classic intelligence analysis and academic studies in international security and geopolitics. She is also a co-founder of the “Cyberladies” NGO, supporting mentorship and inclusion in cybersecurity.
Read more
Explore related topics and insights

