Enhancing cybersecurity through attack simulations
Security teams are often tasked with answering a difficult question: Are we actually protected, or does it just look that way on paper? Breach and Attack Simulation (BAS) was developed to address this exact challenge. Rather than relying on assumptions or occasional testing, BAS introduces a methodical, automated way to validate how well security controls and teams perform under real-world attack conditions.
This article outlines what BAS is, how it integrates with threat intelligence, and how OpenBAS makes continuous, evidence-based security validation both practical and scalable.
What is BAS?
BAS definition
Breach and Attack Simulation (BAS) represents a paradigm shift in cybersecurity validation. Unlike theoretical security measures, BAS provides a platform where security teams can simulate real-world attacks against existing infrastructure and test organizational readiness. Think of BAS as a situational awareness training ground – a virtual battlefield where defenders can test their capabilities against simulated adversaries under realistic conditions.
Organizations invest substantially in security tools, but without validation, these investments often create an illusion of security rather than genuine protection. BAS addresses this reality by providing concrete evidence of defensive capabilities through continuous, automated testing of security controls.
BAS in context of CTI
A BAS program achieves its full potential when integrated with Cyber Threat Intelligence (CTI). This integration creates a dynamic feedback loop between threat intelligence and security validation:
- Threat-Informed defense: BAS enables organizations to generate attack scenarios based on TTPs (Tactics, Techniques, and Procedures) of threat actors targeting their specific industry.
- Contextual testing: Security teams can validate defenses against specific threat actors and campaigns documented in their Threat Intelligence Platform (TIP).
- Risk-Based prioritization: Organizations can focus security improvements on defending against the threats most relevant to their environment.
This intelligence-driven approach ensures that security validation efforts align with the actual threat landscape facing an organization, rather than testing against generic attack patterns. BAS transforms CTI from informational resources into actionable security validation.
BAS vs penetration testing
While traditional penetration tests provide valuable insights, they suffer from significant limitations that BAS addresses:
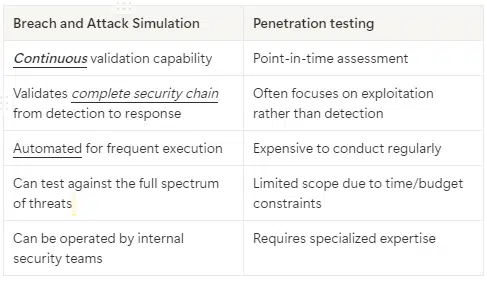
As you can see, BAS complements penetration testing by enabling continuous validation of detection and response capabilities as well as providing ongoing assurance between periodic penetration tests. While penetration tests excel at finding unknown vulnerabilities, BAS excels at validating whether known attack techniques would be detected and effectively countered.
BAS in support of Zero Trust approach
The Zero Trust security model operates on the principle “never trust, always verify.” BAS perfectly aligns with this framework by providing the verification mechanism necessary for Zero Trust implementation:
- Continuous validation: BAS enables ongoing verification that security controls actually work, rather than assuming their effectiveness.
- Assumption challenging: By simulating attacks from various network positions, BAS tests the assumption that compromised assets can’t be used to move laterally.
- Security posture awareness: Provides real-time visibility on security effectiveness based on current threat detection capabilities.

Introducing OpenBAS: a modern approach to Exposure Validation
As organizations adopt frameworks like Zero Trust and shift toward intelligence-driven security, the need for continuous, realistic validation becomes critical. This is where OpenBAS comes in. OpenBAS is an Adversarial Exposure Validation (AEV) platform designed to simulate real-life attack scenarios across technical systems, physical environments, and human behavior. By incorporating prioritized threat intelligence, the MITRE ATT&CK framework, and risk-based employee profiling, OpenBAS identifies the most likely attack paths before they can be exploited. This proactive strategy empowers security teams to reinforce both technical defenses and human readiness, creating a cycle of continuous improvement and resilience against real-world threats.
How can you leverage OpenBAS for your organization?
Test and assess your assets
OpenBAS delivers end-to-end validation of your complete security chain, measuring how well specific controls perform against various attack techniques. The platform identifies detection blind spots, allows you to verify proper security tool configurations, and detects when routine IT changes degrade security effectiveness. For security leaders, OpenBAS provides tangible ROI metrics that transform security from a cost center into a quantifiable business enabler.

Test and assess your teams
Beyond technical validation, OpenBAS builds and measures human capabilities through realistic scenario exercises that challenge detection and response teams. The platform introduces objective performance metrics for detection time and response effectiveness. While OpenBAS offer ways to play traditional tabletop exercises, it can also improves them by generating actual security events requiring real detection and response actions.
Infinite customization possibilities
With its modular, extensible architecture, OpenBAS can be adapted to specific environments through custom collectors or payloads that reflect unique threat landscapes. Organizations also can create industry-specific simulations, compliance-focused validations, and scenarios that replicate sophisticated attack methodologies. The platform’s automation enables continuous validation without manual intervention, while its open source philosophy allows unlimited expansion and customization to match evolving infrastructure and threats.
OpenBAS use cases
Still unsure of where to start? Depending on your security objectives and existing infrastructure, OpenBAS can be deployed in various configurations. Here are three most common use cases:
Threat-informed Defense using a combination of OpenBAS and OpenCTI
OpenBAS is one of the foundation for a threat-informed defense strategy with OpenCTI. Organizations having this use case:
- Align security validation with the MITRE ATT&CK framework
- Develop testing scenarios based on tactics and techniques relevant to their industry thanks to Intelligence gathered from OpenCTI
- Use OpenBAS to validate detection and response capabilities against specific adversary behaviors
- Build a continuous feedback loop between threat intelligence and security controls using the integration between OpenBAS and OpenCTI
- Measure coverage against known adversary techniques to identify defensive gaps
This approach is particularly valuable for organizations facing sophisticated threats and those seeking to mature their security program beyond compliance-driven controls.
Assess your defense against ransomware
OpenBAS helps you validating defenses against one of today’s most disruptive threats—ransomware:
- Develop comprehensive scenarios simulating the complete ransomware attack chain
- Test detection capabilities for early-stage ransomware indicators
- Validate data protection controls and backup integrity
- Exercise incident response procedures specifically for ransomware scenarios
- Test recovery capabilities and business continuity plans
This use case is particularly valuable for organizations in high-risk industries or those that have previously faced ransomware threats.
Run table-top exercises
OpenBAS can also be used as a platform for conducting sophisticated table-top exercises for incident response teams:
- Create dynamic scenarios that unfold over time, simulating evolving security incidents
- Deploy timed communication injects to different stakeholders (executives, PR, legal, technical teams)
- Simulate realistic external pressures
- Test decision-making processes under pressure through escalating scenario complexity
- Evaluate procedural documentation and team coordination effectiveness
- Collect metrics on response time, communication effectiveness, and decision quality
- Identify and address gaps in incident response procedures before real incidents occur
This approach transforms traditional static table-top exercises into dynamic, measurable training experiences that build organizational muscle memory for crisis response. This use case is seeking to validate incident response plans, improve cross-team coordination, and strengthen human-focused security capabilities.
Conclusion
OpenBAS represents a fundamental shift in cybersecurity—moving from “assuming security controls work” to “validating effectiveness through evidence-based testing”. This approach transforms cybersecurity team from a cost center focused on implementing controls to a strategic ccorporate function that demonstrably protects business operations.
The question is no longer whether your security looks good on paper, but whether it actually works against real-world attacks. OpenBAS provides the answer to this critical question—without the devastating costs of finding out through an actual breach.
If you have any question, request, comment or feedback to share with us, don’t hesitate to join us on Slack!
Read more
Explore related topics and insights

