Enhance your Vulnerability Management with Cyber Threat Intelligence
A vulnerability policy is essential for organizations as it provides a structured approach to identifying, assessing, prioritizing, and mitigating security vulnerabilities.
Without a clear policy, vulnerabilities may go unnoticed or unpatched, leaving systems exposed to threats like ransomware and data breaches.
Many cybersecurity frameworks and regulations also require effective vulnerability management. These include ISO 27001, PCI-DSS, the EU’s NIS2 directive, and the Digital Operational Resilience Act (DORA), as well as industry-specific mandates like HIPAA in the U.S. Compliance is often a key driver behind vulnerability management efforts.
To help with this task, vulnerability scanning tools have emerged to give security teams clear visibility into vulnerabilities present across their information systems. However, despite their effectiveness, these tools often reveal an overwhelming (and this is an understatement) number of vulnerabilities, making it challenging to prioritize which ones pose the highest risk and require immediate patching.
As a consequence, timely patch deployment is a struggle, as organizations must balance security updates with business operations to avoid disruptions while limited resources—such as time, staff, and budget—often lead to patch backlogs and an expanded potential attack surface for threat actors.
This article will explore how effective threat intelligence management with OpenCTI can optimize vulnerability policies.
Streamlining Vulnerability Management Prioritization
Prioritization stands as one of the greatest challenges in vulnerability management. While organizations typically encounter thousands of vulnerabilities, each presents a different level of risk.
Rather than applying patches indiscriminately or solely based on CVSS score, organizations can leverage threat intelligence to identify the most urgent updates based on real-world attack data.
OpenCTI offers vital context—including exploitability, active threat campaigns, and attacker tactics—enabling security teams to prioritize vulnerabilities that are most likely to be exploited. This intelligence-driven approach ensures teams address the most critical threats first, minimizing cyber exposure.
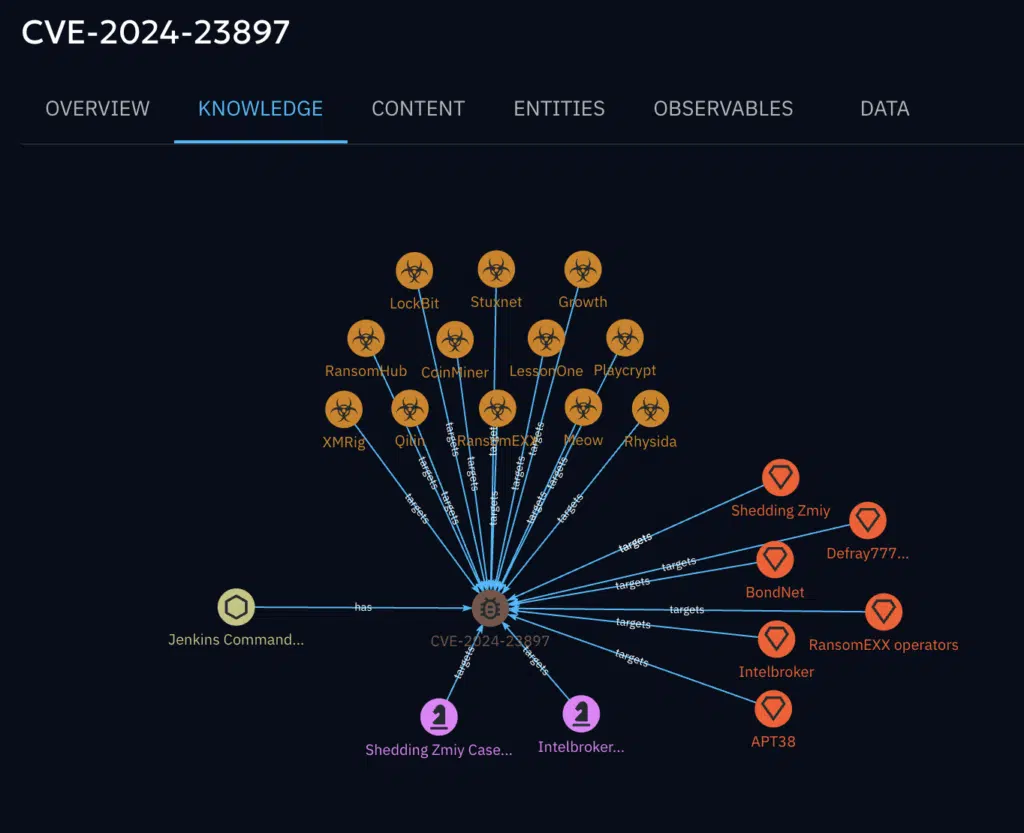
A found vulnerability in Jenkins software targeted by 12 malwares, 6 threat actors and exploited in 2 attack campaigns. This is an example of how OpenCTI can identify a good candidate for emergency patching.
This vulnerability profiling can be done automatically in OpenCTI thanks to the automation playbook engine. The below example show how all the vulnerabilities can be correlated with all the cyber threat intelligence database. In the event of potential threat found, the profile will be saved as a report (called grouping) and notified to the administrator.
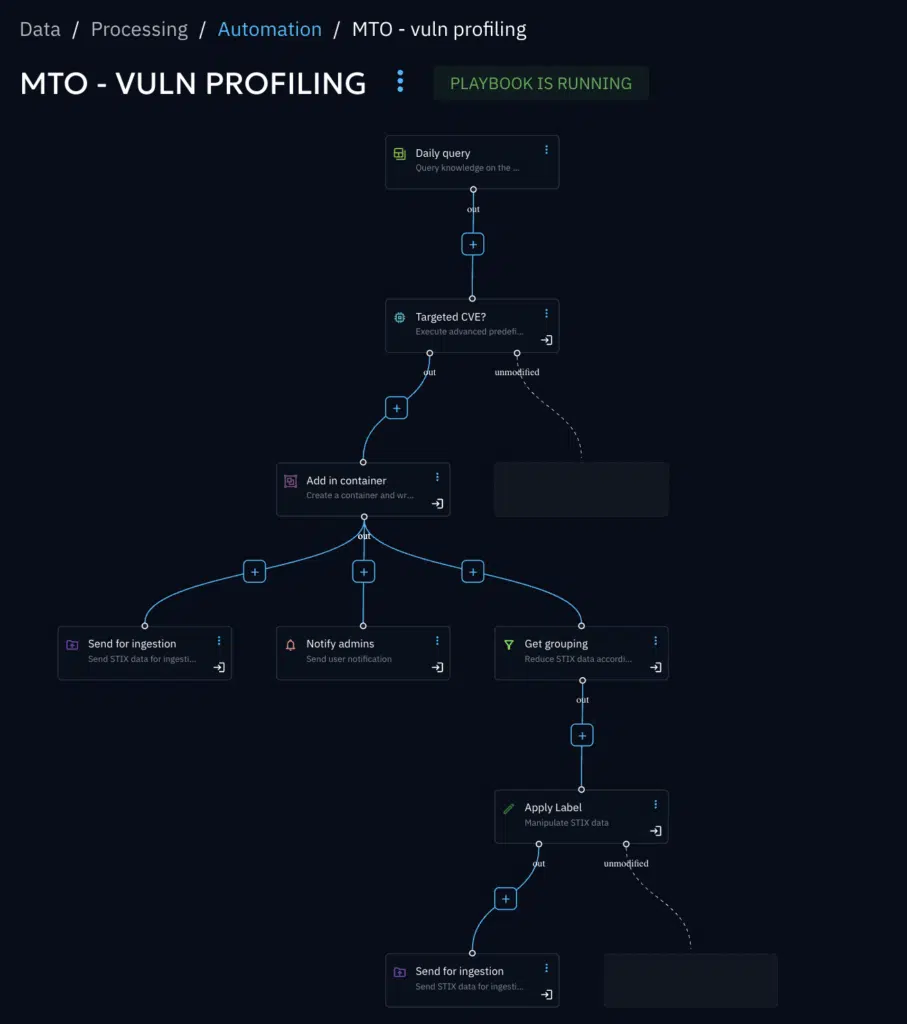
This strategic approach reduces operational disruptions while keeping security teams focused on truly significant vulnerabilities.
Adopting a threat-informed cybersecurity defense
Sometimes patching isn’t possible—whether due to missing fixes/obsolete systems or unavailable maintenance windows (SCADA systems and Windows XP/2012… we are watching you). These situations create significant risks, leaving systems vulnerable, especially when active threats are known to exploit those vulnerabilities.
While virtual patching can help mitigate the risk, this solution isn’t available to everyone. However, you can apply a first layer of protection to mitigate this risk by proactively pushing the indicators that could proactively help you prevent the known threats that are actively exploiting your vulnerabilities.
OpenCTI can enrich the previously obtained profile with the IoC that indicate all the threats that target the given vulnerability. By then pushing all the IOC to your security tools (such as the EDR, Firewalls, proxies, etc), the existing security tools will become threat-informed. Your firewall no longer blocks only random threats, it now blocks the threats targeting the vulnerabilities present in your systems.
The enrichment step of vulnerabilities with associated indicators can be performed with a couple of API calls, the following script is an example of such implementation: https://github.com/marckto-filigran/OCTI-vuln2ioc can
A previous article explained how to push CTI to your security tools, don’t miss it!
Don’t miss a single vulnerability
Keeping up with the latest security vulnerabilities is challenging enough. Tracking all the threats targeting your vulnerabilities adds an entirely new layer of complexity. OpenCTI lets you set up notification rules (“live triggers”) to ensure you never miss any new event related to your specific products.
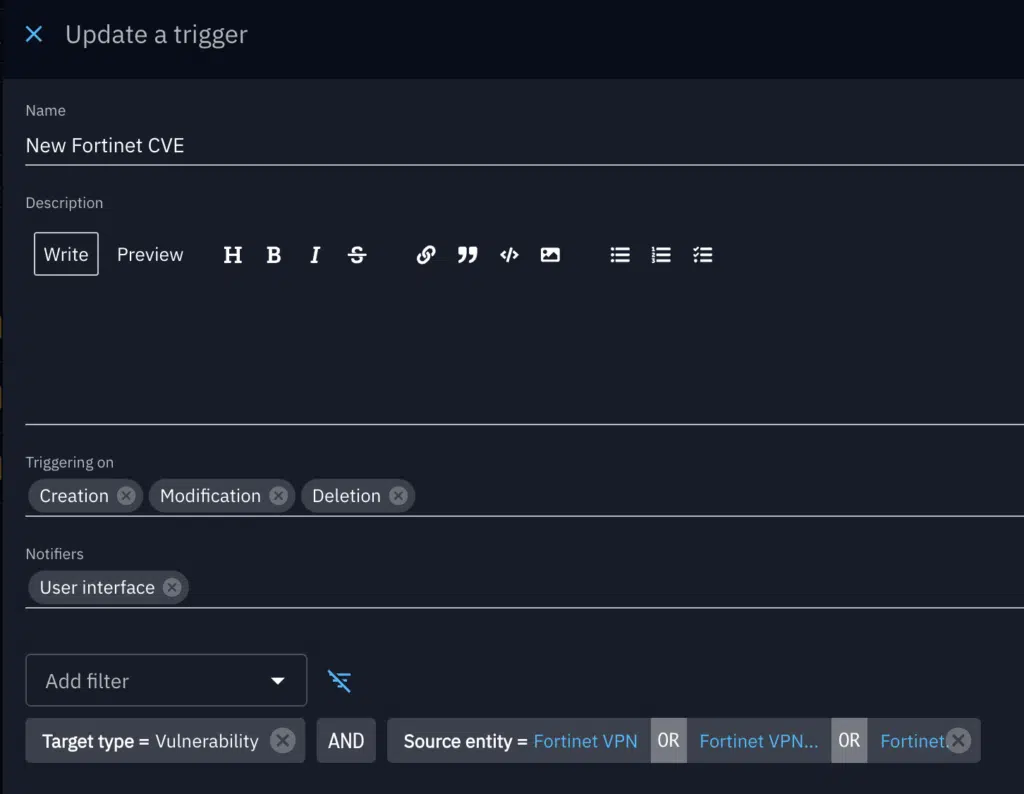
Setting up a Live Trigger is super easy; all you need to do is specify the type of notification you’d like to receive and subscribe to the products you want to monitor.
In the example below, any new vulnerability associated with a Fortinet VPN solution triggers a notification sent directly to the OpenCTI interface.
Conclusion
At first, combining vulnerability management with threat intelligence might not seem intuitive, but the synergy is undeniable. While existing tools for vulnerability management excel at providing internal threat intelligence, they often fall short on external threat intelligence.
OpenCTI bridges this gap, delivering significant value by simplifying the prioritization, triage, and mitigation of threats targeting your vulnerabilities.
If you have any comment, question, feedback, connect with us on slack !
Read more
Explore related topics and insights
