The Cybersecurity Ecosystem as a Dark Fantasy: SOAR, SIEM, and the Key Players
In the world of cybersecurity, defending an organization against relentless adversaries can feel like an epic battle. Automation, detection, intelligence, and human ingenuity come together as a cohesive force, much like characters and tools in a dark fantasy narrative. What if we reimagined these critical components of a cyber defense strategy in this paradigm? Let’s dive into the metaphorical landscape where technology and human expertise intertwine to protect the digital realm.
The Ecosystem Metaphor: Grim Reaper, Oracle, and More
In this reimagined world, the cybersecurity ecosystem becomes a mythical battlefield. Each component of your defense stack assumes a specific role, working together to keep the forces of chaos (threat actors) at bay.
1. SOAR: The Grim Reaper

The Security Orchestration, Automation, and Response (SOAR) platform takes center stage as the Grim Reaper, the executor of decisive actions. It is the ultimate enforcer, automating incident responses, eliminating threats, and carrying out predefined playbooks with ruthless efficiency.
Role: Automates responses, ensures precision, and eradicates threats.
Metaphor: With its glowing scythe, the Grim Reaper cuts down adversaries swiftly and without hesitation. It acts based on the intelligence it receives, making its actions critical to the ecosystem.
2. Threat Intelligence Platform: The Oracle

The Cyber Threat Intelligence Platform (TIP) serves as the Oracle, providing foresight and strategic guidance. It collects and analyzes intelligence from internal and external sources, offering context that enables informed decisions.
Role: Aggregates and contextualizes threat data, offering actionable insights.
Metaphor: Holding a radiant crystal orb, the Oracle foresees incoming threats and whispers insights to the Grim Reaper, enabling swift and accurate responses.
3. SIEM: The Watchtower

The Security Information and Event Management (SIEM) platform is the Watchtower, a vigilant overseer monitoring the digital realm. It collects and correlates logs, raising alarms when anomalies or threats are detected.
Role: Provides centralized visibility, identifies suspicious activities, and feeds intelligence to other components.
Metaphor: From its towering vantage point, the Watchtower surveys the battlefield, illuminating the landscape with red and blue surveillance beams.
4. Detection Platforms (EDR, NDR): The Guards

Detection platforms, such as Endpoint Detection and Response (EDR) and Network Detection and Response (NDR), take on the role of Guards, patrolling their assigned territories. They actively seek and neutralize adversarial activity in endpoints, networks, and beyond.
Role: Detect, investigate, and prevent threats in specific areas of the infrastructure.
Metaphor: Armored and vigilant, the Guards use high-tech tools to identify and challenge any intruder trying to breach the realm.
5. Ticketing Systems: The Scribes

Ticketing systems like ServiceNow or Jira act as the Scribes, diligently recording every action, incident, and resolution. They ensure nothing is overlooked in the fast-paced battle against cyber threats.
Role: Tracks incidents, manages workflows, and ensures accountability.
Metaphor: The Scribes keep meticulous records, documenting the Oracle’s insights, the Watchtower’s alerts, and the Grim Reaper’s actions.
6. Threat Hunters: The Scouts

Threat hunters are the Scouts, venturing into the shadows to uncover hidden threats and adversaries. They proactively seek out dangers that might bypass existing defenses.
Role: Identify active threats, assess gaps in detection, and ensure the ecosystem is prepared for the unknown.
Metaphor: Equipped with glowing searchlights, the Scouts explore dark corners of the digital terrain, returning with critical intelligence.
7. Detection Engineers: The Architects or Smiths

Detection engineers are the Architects or Smiths, responsible for creating and refining the tools and frameworks that power the entire defense system. They design detection rules, tune alerts, and improve automation.
Role: Build, optimize, and maintain detection logic and systems.
Metaphor: Behind the scenes, the Architects forge glowing blueprints and tools, equipping the Guards and empowering the Grim Reaper to execute with precision.
The Synergy: A Unified Force Against Chaos
In this fantasy-inspired paradigm, every component works in harmony:
- The Oracle (TIP) foresees the enemy’s moves, warning the Watchtower (SIEM).
- The Scouts (threat hunters) venture into dark terrain, discovering gaps and bringing valuable insights to the Oracle and Architects.
- The Architects (detection engineers) refine the tools and systems, fortifying defenses.
- The Guards raises alarms and signals the Watchtower (SIEM) to investigate.
- The Grim Reaper (SOAR), empowered by all this intelligence, takes swift and decisive action to neutralize threats.
- Meanwhile, the Scribes (ticketing systems) keep detailed records to ensure accountability and future learning.
The Power of OpenCTI as the Oracle
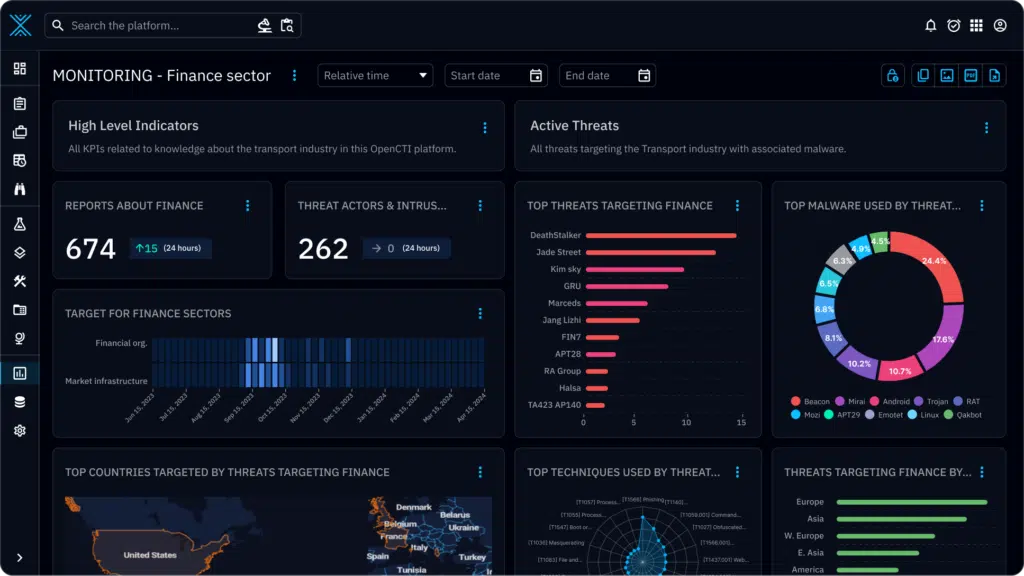
• Central Repository of Knowledge: OpenCTI centralizes threat indicators, campaign data, and adversary profiles, serving as an accessible archive of collective knowledge.
• Actionable Insights: By correlating real-time events with historical data, it highlights patterns and potential attacks in the making—much like an Oracle’s cryptic yet enlightening prophecies.
• Seamless Integrations: Whether feeding your SIEM, enriching alerts for your detection tools, or fueling your SOAR playbooks, OpenCTI’s open architecture ensures that intelligence flows smoothly into every defensive system.
• Community-Driven Development: Its open-source nature invites a global community to refine new “prophecies”—innovative connectors, data models, and enrichment capabilities—that evolve as threats morph and multiply.
Ultimately, the synergy in a well-coordinated cybersecurity operation—Oracle, Grim Reaper, Watchtower, Guards, Scouts, Scribes, and Architects—mirrors the cohesive defense required in a modern Security Operations Center. And with OpenCTI at the heart of it all, you have not just an all-knowing seer but a collaborative, ever-evolving system that guides your organization through the storms of impending threats.
Conclusion: Bringing the Fantasy to Reality
Amidst the swirling energies of this dark fantasy battlefield, each character has a vital purpose: the Grim Reaper (SOAR) wields swift judgment, the Watchtower (SIEM) stands vigilant, the Guards (EDR/NDR) engage in close combat, and the Scouts (threat hunters) traverse unknown terrain. But at the center of it all, the Oracle (your threat intelligence platform) reigns supreme—distilling raw information from across the realm into meaningful insights that guide every action.
In the real world, OpenCTI is the beating heart of this oracle-like function. Through robust integrations and open-source flexibility, it aggregates, enriches, and contextualizes threat data to illuminate the ever-shifting landscape of adversarial tactics. Just like the Oracle of myth, OpenCTI peers into the future, gathering wisdom from external sources—ISAC feeds, vulnerability databases, dark web chatter—and internal sources like incident records and telemetry. It offers foresight not only to the Grim Reaper (SOAR) for automated responses but also to your Watchtower (SIEM) so it can focus its gaze where it matters most.
If you have any question, request, comment or feedback to share with us, don’t hesitate to join us on Slack!
Read more
Explore related topics and insights
