Retail’s Vulnerabilities Exposed: Check Your Defenses Against DragonForce Ransomware
The UK retail sector has experienced a significant escalation of cyber threats in the recent weeks. In a series of high-profile attacks, major retailers including Marks & Spencer, Co-op and Harrods have been impacted. They all reported cyber incidents that taregted their payment systems, inventory, payroll and other critical business functions.
Marks & Spencer suffered an online sales outage, with problems beginning during the Easter weekend and still ongoing while this article was published. Their losses have been estimated to be in tune of £3.8m per day. Co-op’s data breach affected their customer information including names and contact details. Their IT systems were forced to shut down temporarily and 200 of its 2,300 stores across the UK had been affected by an issue with their contactless payment systems. Harrods claimed to have taken a swift action to contain its breach after attempts to gain unauthorized access to their systems.
All these high-profile attacks are reportedly linked with a single ransomware group, DragonForce.
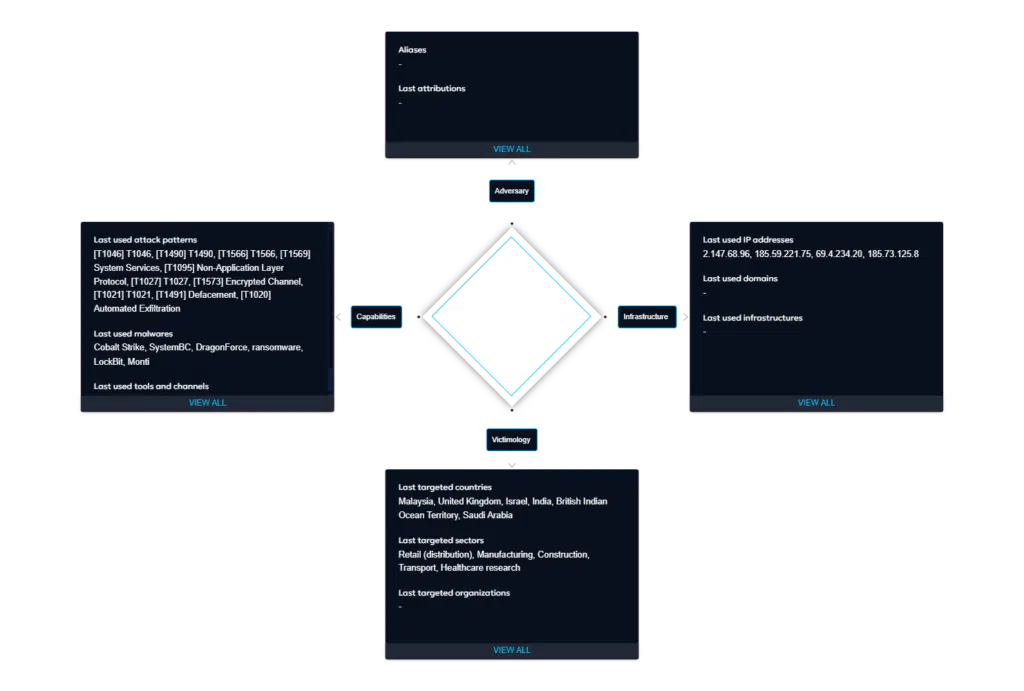
Ransomware-as-a-Service?
DragonForce is a relatively new ransomware operation that became known in late 2023. Originally emerging from Malaysia as a hacktivist collective, DragonForce has evolved into a sophisticated Ransomware-as-a-Service (RaaS) operation, offering affiliates customizable ransomware kits and infrastructure support. DragonForce operators manage the backend — including malware development, leak site hosting, and ransom negotiations. In return, they take a 20% share of any ransom payments.
Anonymous individuals identifying as members of the DragonForce groups have claimed responsibility behind these latest cyber attacks on UK retailers. They even contacted several media houses with evidence about infiltration and stealing of customer and employee data.
It is worth noting here that this is not the first series of attacks unperpinned by DragonForce. They are understood to be behind a number of cyber-attacks in APAC and US, including on Honolulu OTS (Oahu Transit Services), Coca-Cola (Singapore) and Yakult Australia.
According to SentinelOne, DragonForce operators commonly use a blend of phishing campaigns — with malicious links or attachments, alongside scanning for unpatched vulnerabilities in internet-facing systems.
They’ve previously taken advantage of high-impact exploits like Log4Shell in Apache Log4j2 and multiple vulnerabilities in Ivanti Connect Secure. In parallel, they often attempt credential stuffing attacks on RDP and VPN portals using leaked username-password combinations.
The DragonForce ransomware gang is believed to be working with English-speaking threat actors with tactics in line with Scattered Spider, a partnership working together for these recent attacks as well. Scattered Spider focuses heavily on social engineering, identity theft and manipulating human trust.
Researchers at Google Threat Intelligence Group (GTIG) said in a recent report that DragonForce’s operators recently claimed takeover of RansomHub, a ransomware-as-a-service (RaaS) syndicate’s set of tools that Scattered Spider members used in the past, after it ceased operations in March.
Are you protected?
For the latest attacks on retailers, attackers exploited human vulnerabilities, with persistent social engineering techniques, impersonating as employees and convincing IT help desks to reset passwords, giving them a foothold inside corporate systems.
Defending the technical perimeter is not enough anymore. While patching vulnerabilities and hardening systems remain essential, attackers are increasingly exploiting the human layer — in this case, tricking IT help desks into resetting credentials through well-crafted social engineering.
UK’s National Cyber Security Centre (NCSC) has recommended that all companies review their help desk processes to detect and block these types of breaches. They are advising companies to pay specific attention to different Admin accounts (domain, enterprise and cloud admins for example) and to check that their access is legitimate at all times. In addition, companies should ensure that they have to ability to consume and understand Techniques, Tactics and Procedures (TTP) sources from threat intelligence rapidly while being able to response accordingly. Attacks like this are becoming more and more common and all organizations, of all sizes, need to be prepared.
Check your defenses
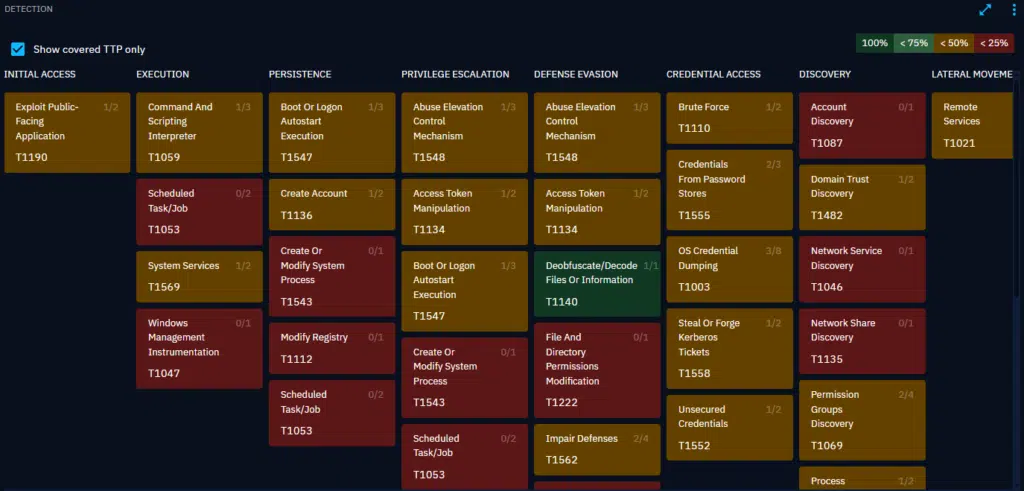
One of the crucial steps in defending your organization is to test your existing controls. Check your EDR and SIEM configurations and your SOC response against DragonForce. You can do it easily with our breach and attack simulation platform, OpenBAS. Its open-source and freely available. A pre-packaged DragonForce ransomware scenario is available for you to download too. Here are some of the links we have provided that you will find useful:
Once you deploy OpenBAS platform and have logged into the console, you should install the agents on some test systems in your environment that are configured with the security controls that you wish to test, such as EDR and SIEM, and also connect OpenBAS to the APIs on those controls so that it can validate if the controls prevented and detected each stage of the attack.
Import and run the scenario
Once you have OpenBAS running in your environment, you can then import and run the scenario itself using the instructions below.
- Click on Scenarios.
- Click on the Import icon.
- Select the DragonForce scenario zip file you downloaded (do not unzip it first).
This will import the DragonForce scenario, and open it for you.
4. Click on the Injects tab to view the predefined injects in the scenario that will simulate an attack. If it starts in Timeline view, then click the grid view icon to get the view below.
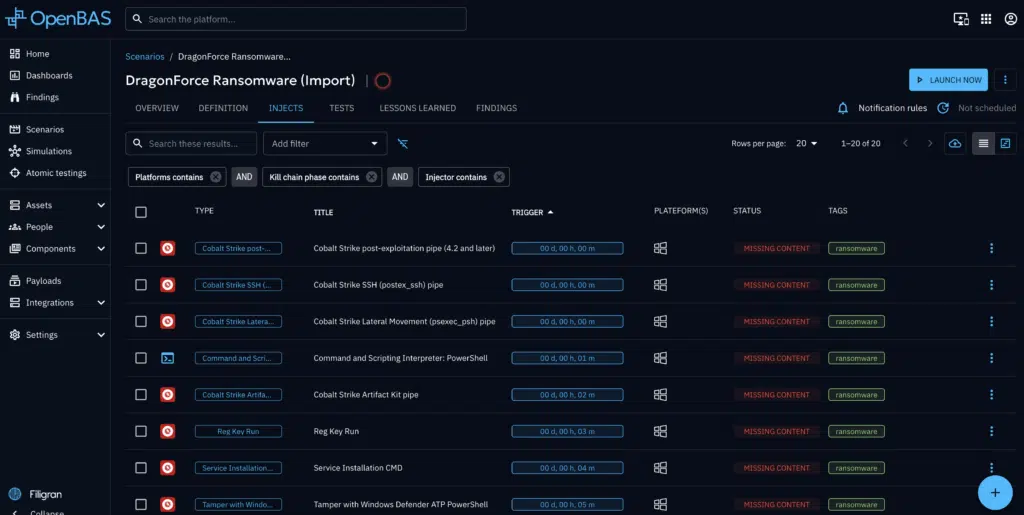
5. To assign assets to run the scenario, select all injects using the checkbox, and then click the bulk edit button that pops up. Use the bulk edit to add your assets to the injects.
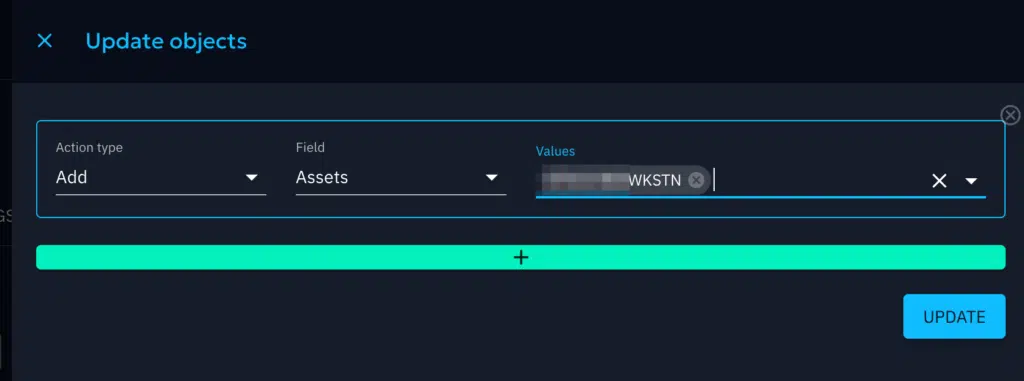
6. Once assets have been added, you can run the scenario.
7. The simulated DragonForce attack will appear in Simulations. If you click into this, you can view the results of each inject; green shows the control was successful, and red shows that it failed.
8. You can use these results to view the controls that would fail, and then add or modify configuration to your SIEM or EDR to be more successful next time.
Click here to read more on this scenario and its construction together with AtomicRedTeam.
Continuously Test and Validate
Ransomware groups like DragonForce follow a clear sequence of behaviors. Tracking and understanding their TTPs overtime is important to firm-up your defenses. OpenBAS allows you to schedule recurring scenarios and use alerts to get visibility into performance of your different security tools as well as how your different security teams respond. In this scenario, you can utilise OpenBAS to test and adapt to not only your prevention and detection results but also performance of your Admin team, from within a single platform.
Stop attacks before they materialize, elevate your security posture on technical and human side!
Conclusion
These recent retail attacks are a sharp reminder that even well-defended organizations remain exposed to tactics that bypass technical controls entirely. A resilient security posture must assess both sides of the equation: technical controls and human readiness. Simulating how staff respond under pressure, validating processes like identity verification, and reinforcing security awareness are just as vital as vulnerability scanning and threat detection. Both layers must work together to prevent compromise.
Join us on our Slack community channel to tell us what you think!
Read more
Explore related topics and insights


