Validate Your Defenses Against SharePoint Exploits with OpenCTI and OpenBAS
Ransomware operators and Nation States actors are increasingly exploiting Microsoft SharePoint vulnerabilities to gain a foothold in enterprise networks. Attackers are leveraging unpatched on-premise Sharepoint servers, chaining exploits to escalate privileges, and deploying ransomware payloads in targeted environments. The attack is affecting 100s of organizations including government agencies.
This post outlines how to check whether your organization is exposed, and how you can use OpenCTI and OpenBAS to both understand and validate your defenses against these threats.
We strongly advise you to follow Microsoft Customer guidance for SharePoint vulnerability CVE-2025-53770
The Microsoft SharePoint Zero-Day Exploitation Risk
Recent threat intelligence reveals the active use of the following SharePoint vulnerabilities in ransomware intrusion chains:
- CVE-2025-53770 (”Toolshell) – Remote Code Execution Vulnerability
- CVE‑2025‑53771 – Bypasses authentication protection
These two vulnerabilities are typically chained together. While CVE‑2025‑53771 is used to spoof HTTP headers (e.g., X-RequestDigest, Referer) so that SharePoint accepts the request as valid, CVE‑2025‑53770 is used to send a malicious serialized payload, triggering remote code execution. Amongst the reported post exploitation activity, researchers have noted webshells being deployed, privilege escalation, and machine key theft (for persistence).
While this article outlines steps defenders can take to bolster defenses using OpenCTI and OpenBAS against threats like Toolshell, it is not a replacement of official vendor-customer guidance.
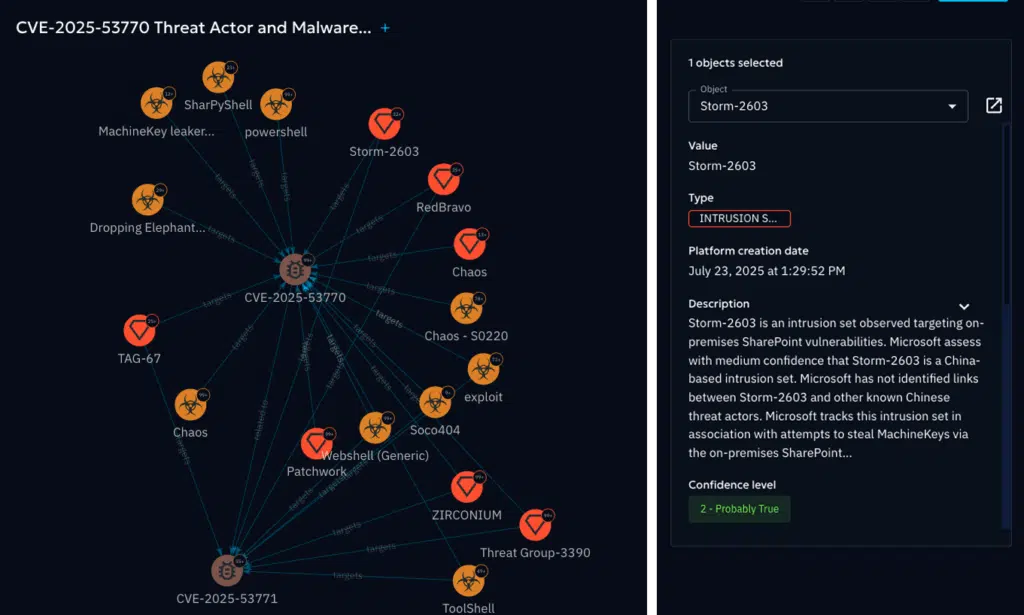
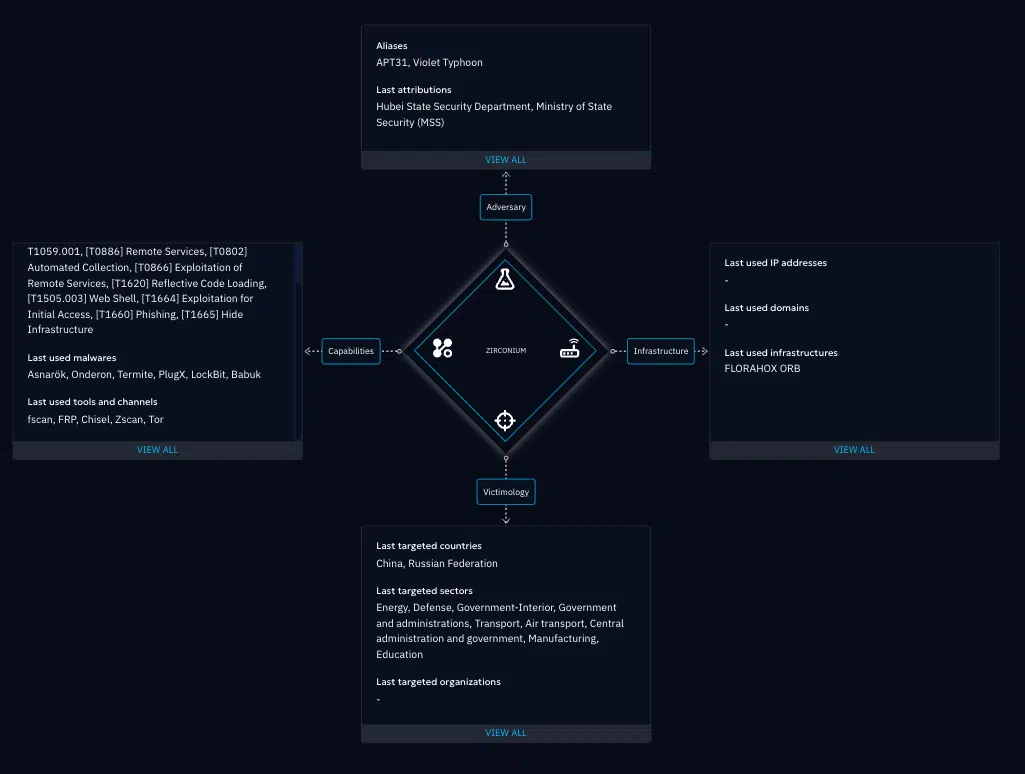
Using OpenCTI’s Knowledge Graph we can represent and further create Threat Actor and Malware relationships to CVE-2025-53770.
Step 1 – Validate Exposure using OpenBAS
OpenBAS can be used to validate your vulnerable exposure to threats.
Are you running affected versions of SharePoint?
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Server Subscription Edition
Have you applied the security updates?
- CVE-2025-53770: Patched on the 20th of July, 2025.
- CVE-2025-53771-: Patched on the 20th of July, 2025.
If you’re unsure whether these patches have been applied, or whether these versions are in use, test for exposure.
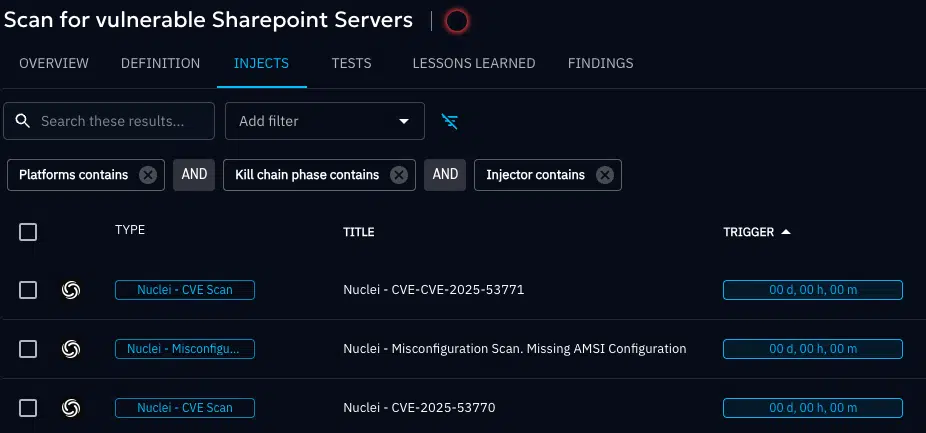
OpenBAS is a breach and attack simulation tool, allowing you to simulate real threat scenarios against your environment. Using the OpenBAS integration with Nuclei you can immediately launch agent-less scans against your assets, including your internet facing webservers and Sharpoint servers.
Review any playbooks on the XTM Hub that can be modified for your use-case
Filigran has published a number of technical scenarios to the XTM community that can be personlised and modified for your use-case.
Create/Import a Nuclei scan to validate exposure
Create your own or import existing Nuclei templates that can be easily imported into OpenBAS and ran against your infrastructure.
Validate your defenses
Run the test through a combination of executors such as the OpenBAS agent, the Nuclei scanner, and your EDRs. Collect the results based on integrations with your SIEM, EDR and responses on the machine to see if you are vulnerable.
The result will allow you to understand if you have prevention or detection defenses and wether the vulnerability can be exploited.

Schedule and Repeat
Schedule the created OpenBAS Scenario and run it every 12-24 hours to continuously validate your defenses until you have everything under 100% control. Repeat patching, security hardening, and locking down any unnecessary services until your BAS result is delivering results that your happy with. Leverage the remediation recommendations that Microsoft and OpenBAS provide.
Step 2 – Understand the Threat using OpenCTI
OpenCTI enables cyber threat intelligence teams to collect, correlate, and contextualize threat data, helping you understand the full threat landscape behind these vulnerabilities.
What OpenCTI enables:
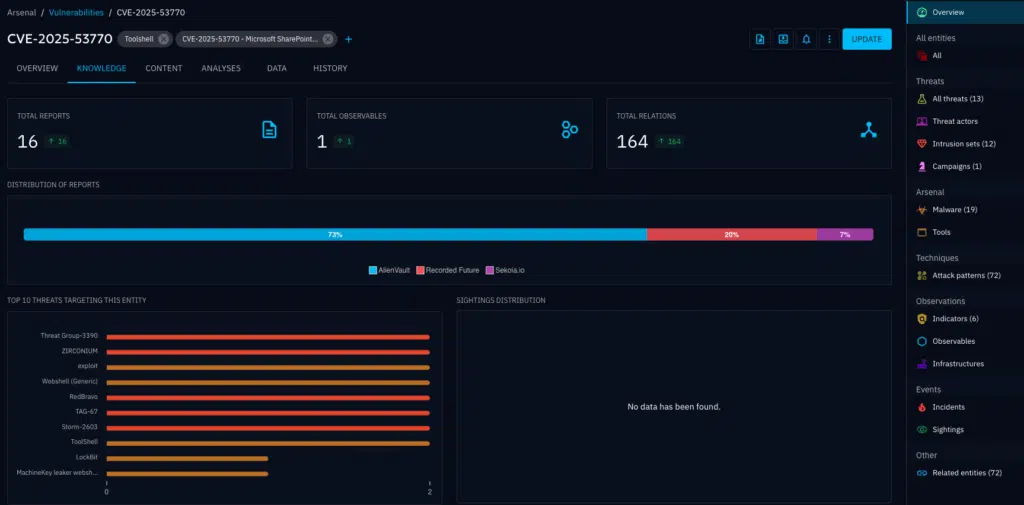
1. Vulnerability-Centric Intelligence
OpenCTI ingests and normalizes CVE data across multiple feeds (e.g., NVD, CIRCL, MISP), allowing you to:
- Identify systems impacted
- Link CVEs to threat actors, intrusion sets, and malware families
- Map CVEs to MITRE ATT&CK techniques (e.g. T1078 – Valid Accounts, T1059 – Command and Scripting Interpreter)
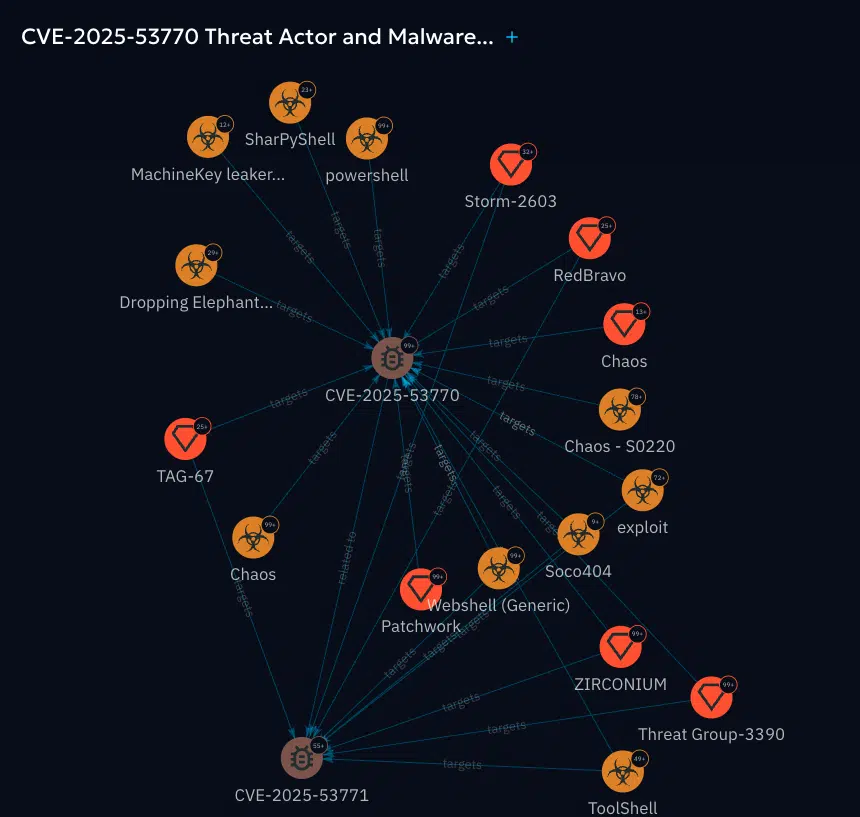
2. Threat Actor Correlation
With OpenCTI, you can:
- Monitor threat actors known to exploit SharePoint
- Link these actors to campaigns and toolsets
- Build internal risk profiles based on real-world intelligence
3. Asset Prioritization
Integrate OpenCTI with your security logs (SIEM, EDR) and asset inventory and vulnerability scanner to cross-reference and be alerted on:
- post exploitation behaviour in your environment
- New TTPs and Attackers being linked to the vulnerability.
- Evolving Exploitation status (theoretical vs. active across Nation States vs Commodity Malware adoption)
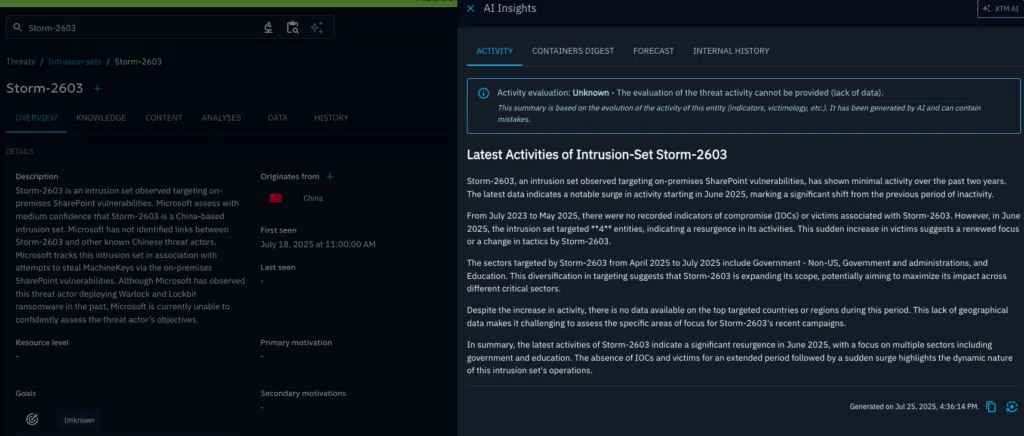
Step 3 – Automate Hunt for Threat Actor behaviour
Leverage existing threat intelligence across open-source and closed source communities in OpenCTI in combination with the automation playbooks to create custom hunting feeds for CVE-2025-53770.
With a few clicks you can create no-code playbooks that send Yara, Snort, Suricata rules into your security tools, collected from your global threat intelligence sources, while collecting, enriching, and labelling IOCs that might go into a blocking list or are used for detection.
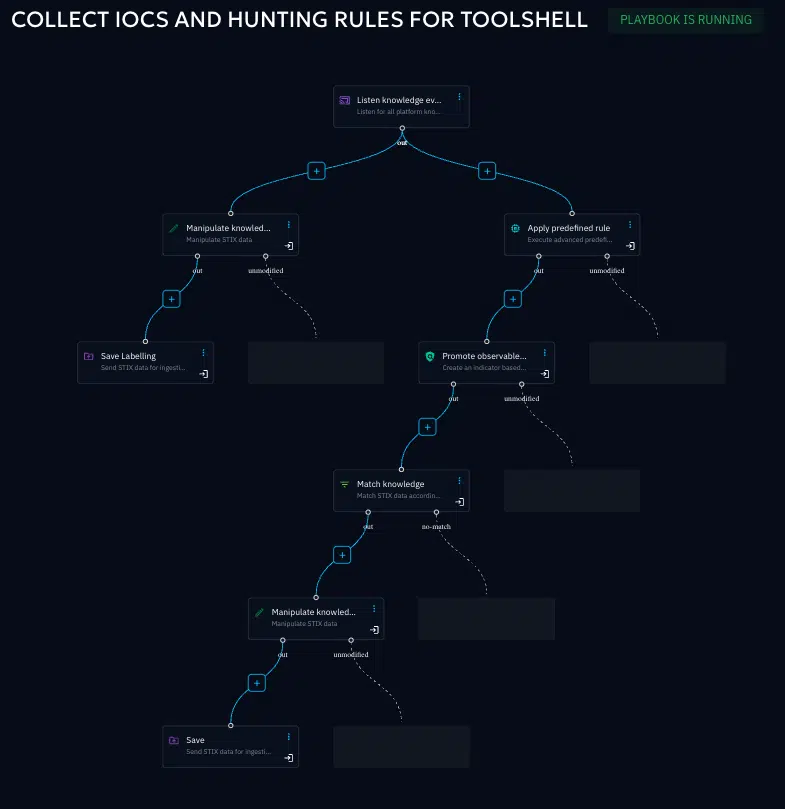
This playbook collects all knowledge events in OpenCTI, strips them of their IOCs, labels them and then sends them straight into the SIEM for high-priority detection use-cases.
Step 4 – Intelligence Led Testing and Defenses
OpenBAS is a breach and attack simulation platform that helps you safely emulate SharePoint exploit chains in your own environment without real impact. But once you’ve mitigated and tested against the threat you can also use the combination of OpenCTI and OpenBAS to create automated end-to-end breach scenarios to test your response time to specific exploit events, test your Ransomware Incident Response plan and simulate APT behaviour in your environment to fix technical miscon
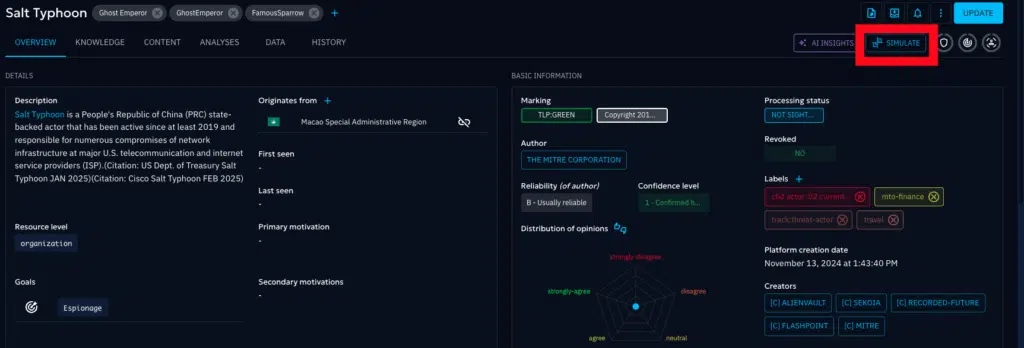
Simulate Intelligence-led Attack Scenarios
Run simulations that replicate the actual steps used to exploit SharePoint and simulate behaviour by threat actors step for step.
- Choose a scenario in OpenCTI based on your interest in a Threat Actor, Vulnerability, or Threat Campaign.
- Click on simulate and OpenCTI will automatically spawn a scenario in OpenBAS with attack payloads mapped to the Attack Patterns reported for the given threat intelligence.
Validate Your Detection Pipeline
Test whether your current stack detects and responds to:
- Suspicious Sharepoint abuse
- Unusual access tokens or privilege escalation
- Command execution from SharePoint processes
Or any other TTP identified by your Threat Intelligence in OpenCTI as being currently used in attack campaigns against your sector, tech stack, or geography.
Summary
The ongoing zero-day exploitation of SharePoint is real and active especially for your hybrid and enterprise environments. Ensure that you make use of tools like OpenCTI and OpenBAS to:
- Understand the threat from both a technical and strategic perspective
- Map threat intelligence directly to internal exposures
- Continuously validate whether detection and response mechanisms are ready
Feel free to ask any questions about it on our Slack community channel
And if you are looking for any help in building your threat management or simulation program, contact the Filigran team or request a proof of concept deployment for your environment.
Read more
Explore related topics and insights

