How SEAL enhances Web3 security with OpenCTI – and how you can too!
The Security Alliance (SEAL) operates a threat intel sharing initiative called SEAL Intel for the Web3 and cryptocurrency ecosystem. SEAL has adopted OpenCTI as its platform of choice to ensure compatibility with traditional threat intel sharing standards like STIX while supporting the unique needs of the Web3 ecosystem.
OpenCTI has transformed SEAL’s ability to collect, analyze, and share critical intelligence about threat actors in the Web3 space. The platform enables real-time ingestion, processing, analysis, and intelligence sharing with trusted partners across the ecosystem.
By combining data from over 100 professionals and organizations with intelligence from major security firms, SEAL has significantly improved its ability to identify malicious patterns and coordinate defensive responses across the cryptocurrency community. We encourage others in the cryptocurrency industry to enhance their security posture by adopting a STIX-compatible platform like OpenCTI.
Why Implement OpenCTI for Web3 Security?
OpenCTI serves as a comprehensive intelligence repository and analytical engine for understanding Web3 threats. It collects, organizes, and visualizes information about malicious actors, their techniques, and the relationships between seemingly disparate incidents.
For example, OpenCTI allows us to map connections between specific wallet addresses used across multiple phishing campaigns, revealing larger criminal operations that might otherwise appear as isolated events. These capabilities led SEAL to select OpenCTI as our central threat intelligence platform, addressing critical shortcomings we experienced with informal sharing methods. We identified three key advantages that made OpenCTI the clear choice for SEAL Intel:
Enhanced Threat Detection with Standardized Intelligence Formats
OpenCTI leverages industry-standard threat intelligence formats like STIX/TAXII, enabling SEAL to ingest, analyze, and share threat data in a structured, machine-readable way. Unlike informal channels such as Telegram groups, where intelligence sharing is ad hoc and unstructured, OpenCTI’s standardized approach ensures data consistency, reliability, and interoperability.
When the SEAL Phishing Bot identifies a new malicious domain, it’s automatically formatted as a STIX object with proper relationships and indicators for automated analysis and correlation with existing threats. In contrast, Telegram shares IOCs as plain text without context, proper tagging, or verification mechanisms, making the data prone to false positives and difficult to integrate into automated security tools. OpenCTI also enforces proper threat classification using the MITRE ATT&CK framework, ensuring each indicator includes critical context such as confidence scores, handling requirements, and expiration dates – features that informal channels cannot provide.
Advanced Relationship Mapping Through Graph Visualization
Understanding the connections between actors, campaigns, and infrastructure is critical when analyzing Web3 threats. While Telegram offers linear conversation threads where relationships between threat actors or campaigns become lost in the noise, OpenCTI’s graph database foundation enables sophisticated entity relationship analysis.
Telegram cannot link related threats across messages, lacks version control for updated intelligence, and cannot visually map how wallet addresses, domains, and threat actors connect in complex attack chains. OpenCTI provides these critical visualization capabilities, allowing analysts to discover non-obvious connections hidden in chat-based platforms.
Secure Intelligence Sharing Within a Trusted Community
OpenCTI implements granular permission controls and audit trails that are absent in Telegram and similar messaging platforms. Telegram groups cannot track who accessed specific intelligence, compartmentalize sensitive information, or formally attribute intelligence sources.
These deficiencies create significant opsec risks, as threat actors commonly infiltrate public security channels to monitor defensive strategies. OpenCTI’s structured sharing protocols include mandatory source attribution, confidence scoring, and access tracking, creating an intelligence ecosystem where partners can trust the provenance and reliability of shared data.
When should my organization adopt OpenCTI?
For smaller security teams who want to read and occasionally contribute to threat intelligence collected by SEAL, you can register a new account on the SEAL Intel managed platform. Our platform is free. However, larger organizations and those with proprietary intelligence may consider adopting OpenCTI internally.
SEAL Intel uses OpenCTI to create a comprehensive threat intelligence ecosystem that combines data from over 100 professionals and organizations with intelligence from major security firms. This integration has significantly enhanced our ability to identify malicious patterns and coordinate defensive responses across the cryptocurrency community. We encourage others in the cryptocurrency industry to strengthen their security posture by adopting a STIX-compatible platform like OpenCTI.
| SEAL Intel | Internal OpenCTI | |
|---|---|---|
| Pros |
|
|
| Cons |
|
|
Getting the most out of OpenCTI
While these advantages highlight why we chose OpenCTI, our practical implementation demonstrates how other security teams can effectively deploy this platform to address Web3-specific threats. Below, we outline our approach for configuring and utilizing OpenCTI, providing a blueprint organizations can follow to establish an internal threat intelligence capability. These components have helped us address Web3 security concerns while maintaining interoperability with broader security operations.
Multi-Source Data Ingestion Architecture
SEAL has configured OpenCTI to ingest threat data from diverse sources across the Web3 ecosystem. Our implementation includes automated connectors that pull daily entity updates from partners like MetaMask, Doppel, Wallet Guard, and ChainPatrol.
Organizations building their own instance can leverage OpenCTI’s connector framework to integrate with public threat feeds and proprietary sources. For example, we’ve developed custom connectors for the SEAL Phishing Bot that automatically format newly discovered threats as STIX objects, and other teams can replicate this for their detection tools.
Web3-Specific Indicator Management
Beyond traditional IOCs like malicious domains and IP addresses, our OpenCTI implementation tracks cryptocurrency-specific indicators, including wallet addresses associated with scams, malicious smart contracts across multiple blockchains, and exchanges laundering stolen assets.
Any organization can extend its OpenCTI instance with custom observable types and taxonomies tailored to Web3 threats, allowing for comprehensive tracking of both conventional and blockchain-specific indicators in a unified platform.
Relationship Analysis for Attribution
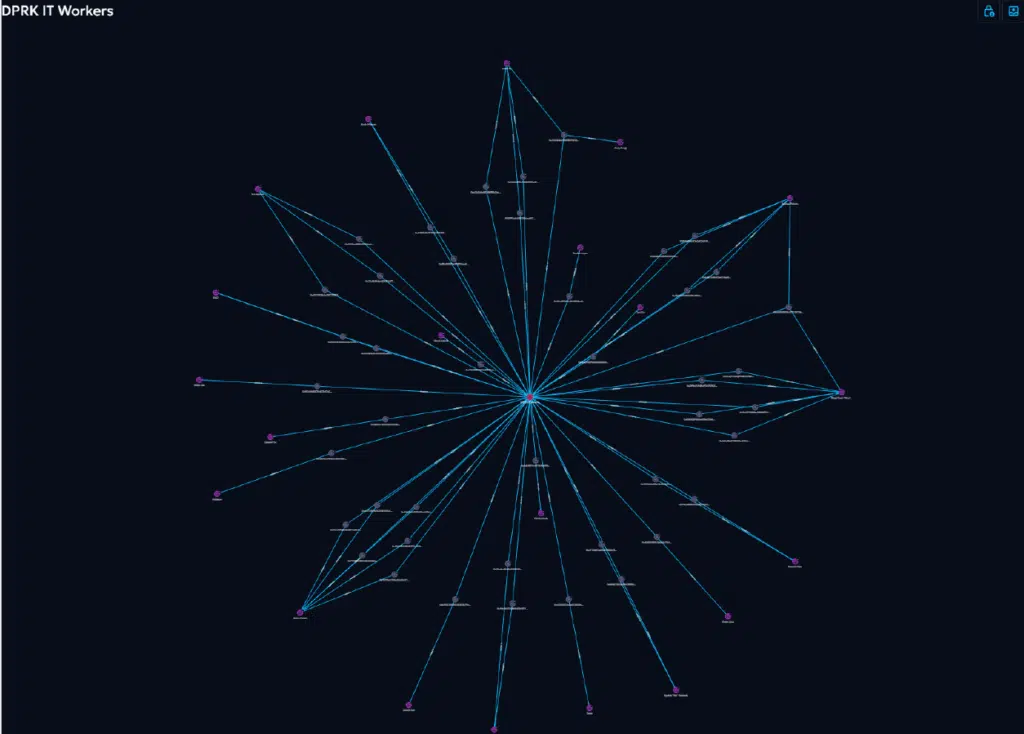
SEAL analysts leverage OpenCTI’s graph database foundation to map connections between seemingly unrelated incidents. For instance, we’ve used relationship visualization to attribute multiple phishing campaigns to specific threat actors like DPRK IT workers by connecting wallet addresses, infrastructure patterns, and tactical similarities. Other security teams can replicate this capability in their OpenCTI instance by establishing relationship types and implementing consistent tagging practices to support complex entity relationship analysis.
Operational Integration Pathways
We’ve integrated OpenCTI with various security tools to create automated workflows with connectors that feed indicators directly into SIEMs, EDRs, and firewall systems, allowing us to automatically block known threats. SEAL is also working with Gauntlet to create documentation that can help other organizations establish integrations with their existing security infrastructure. We want to make this capability more accessible across the ecosystem.
Conclusion
Through OpenCTI’s advantages, we’ve proven the value of open-source threat intelligence platforms for addressing unique security challenges in Web3, cryptocurrency, and decentralized networks. SEAL Intel serves as a force multiplier for the entire cryptocurrency security community with an established central hub for intelligence collection, analysis, and sharing.
About SEAL
The Security Alliance (SEAL) is a 501(c)(3) non-profit on a mission to secure the future of crypto using innovative projects, elite technologists, and social coordination to drive meaningful adoption of secure practices. Current initiatives include legal protections for white hat security researchers; standards building; and free services in incident response, red teaming, and threat intelligence sharing.
Read more
Explore related topics and insights
